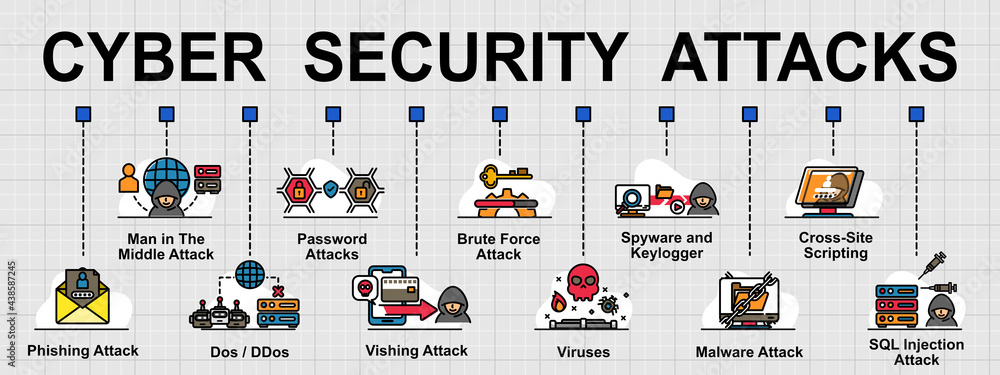
Vector banner of general cyber security attacks. Creative flat design for web banner ,business presentation and online article. Stock Vector | Adobe Stock

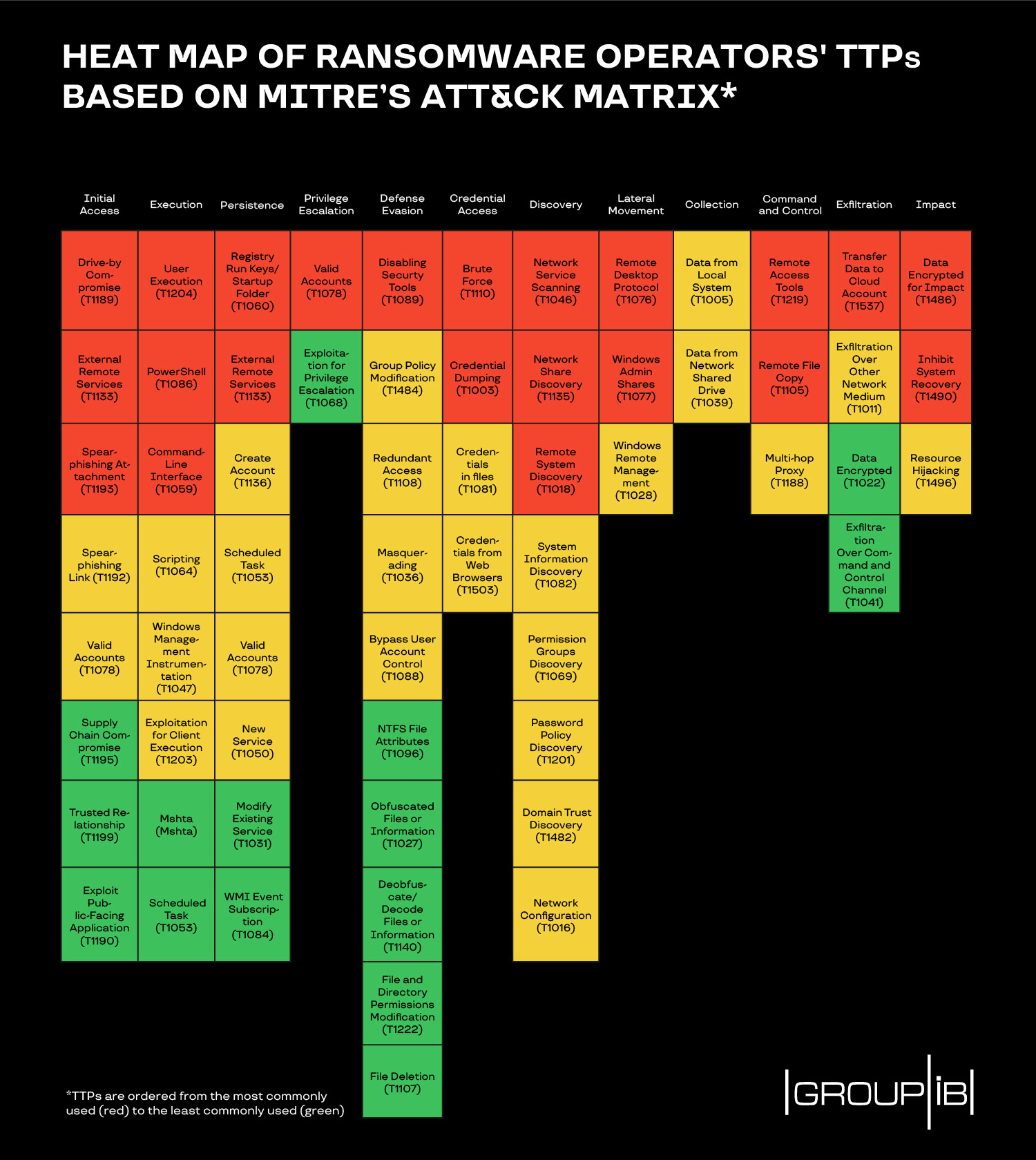
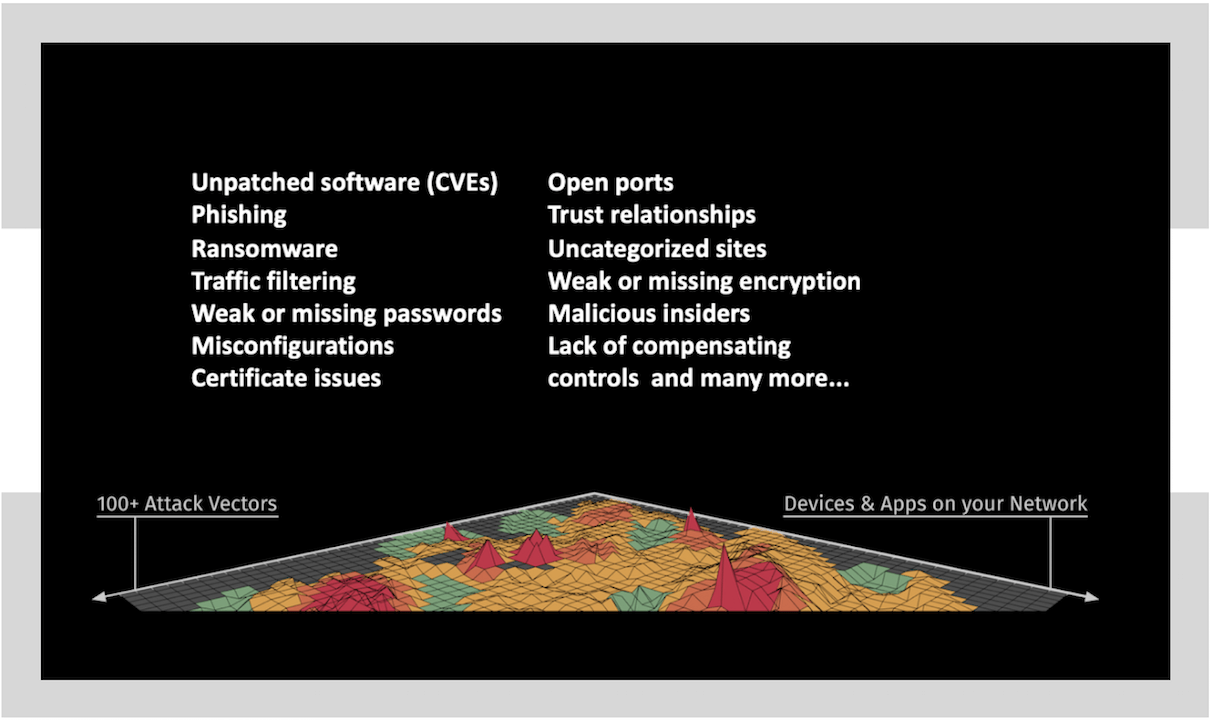
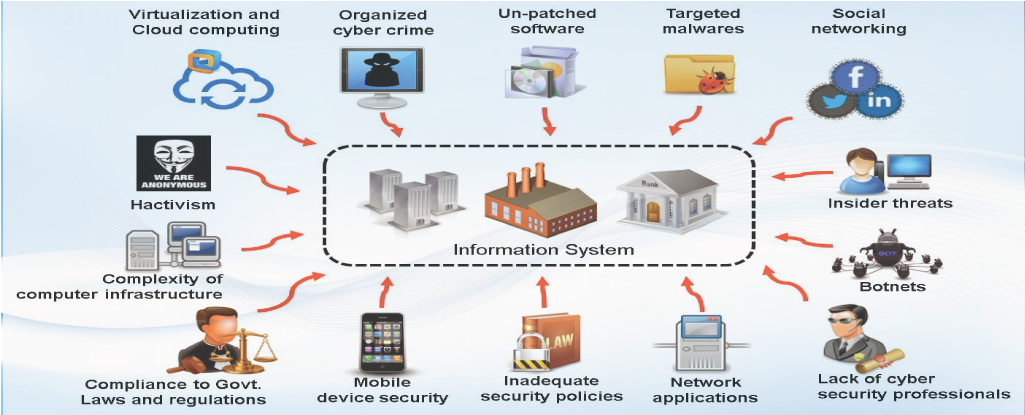
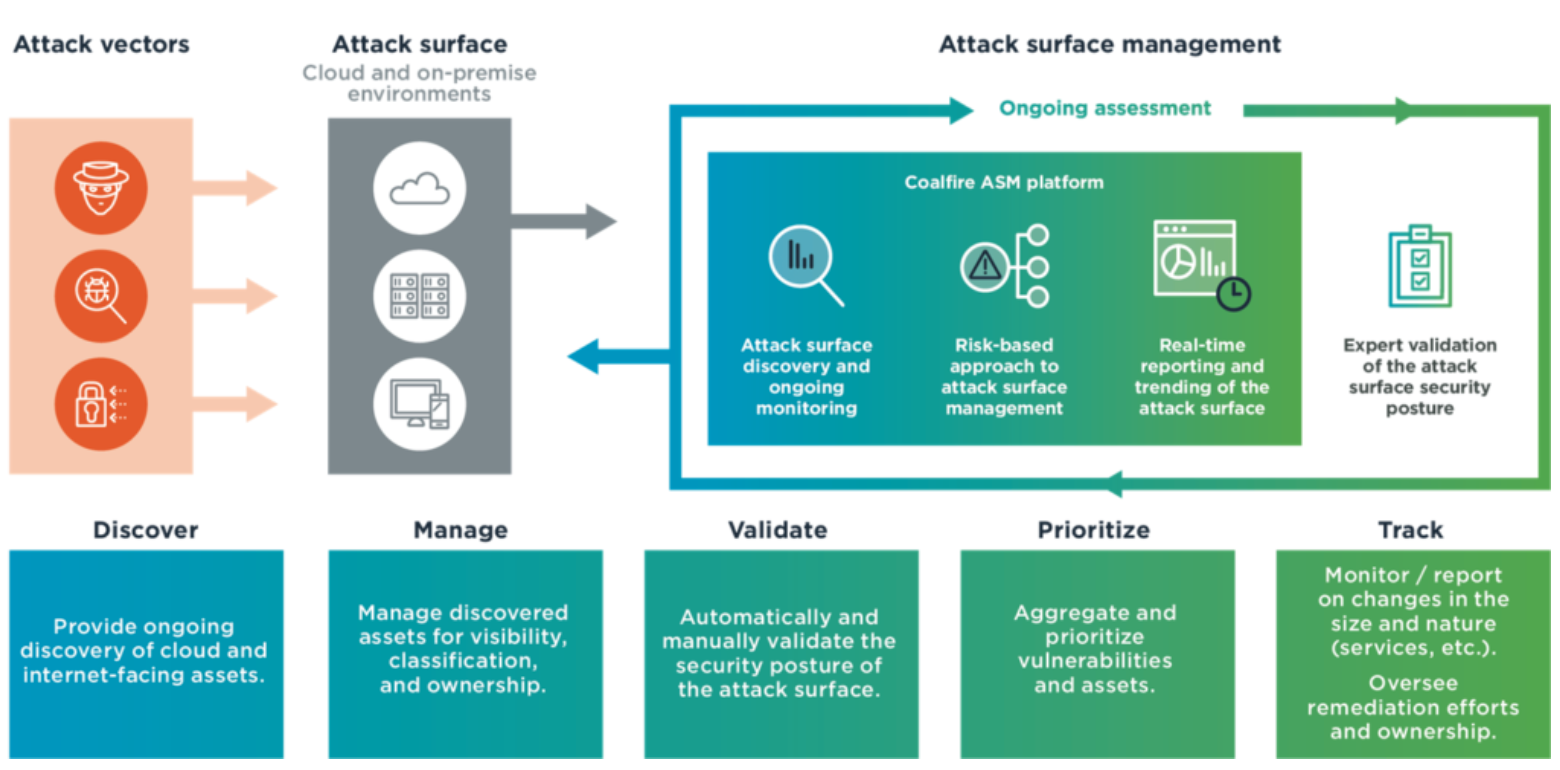
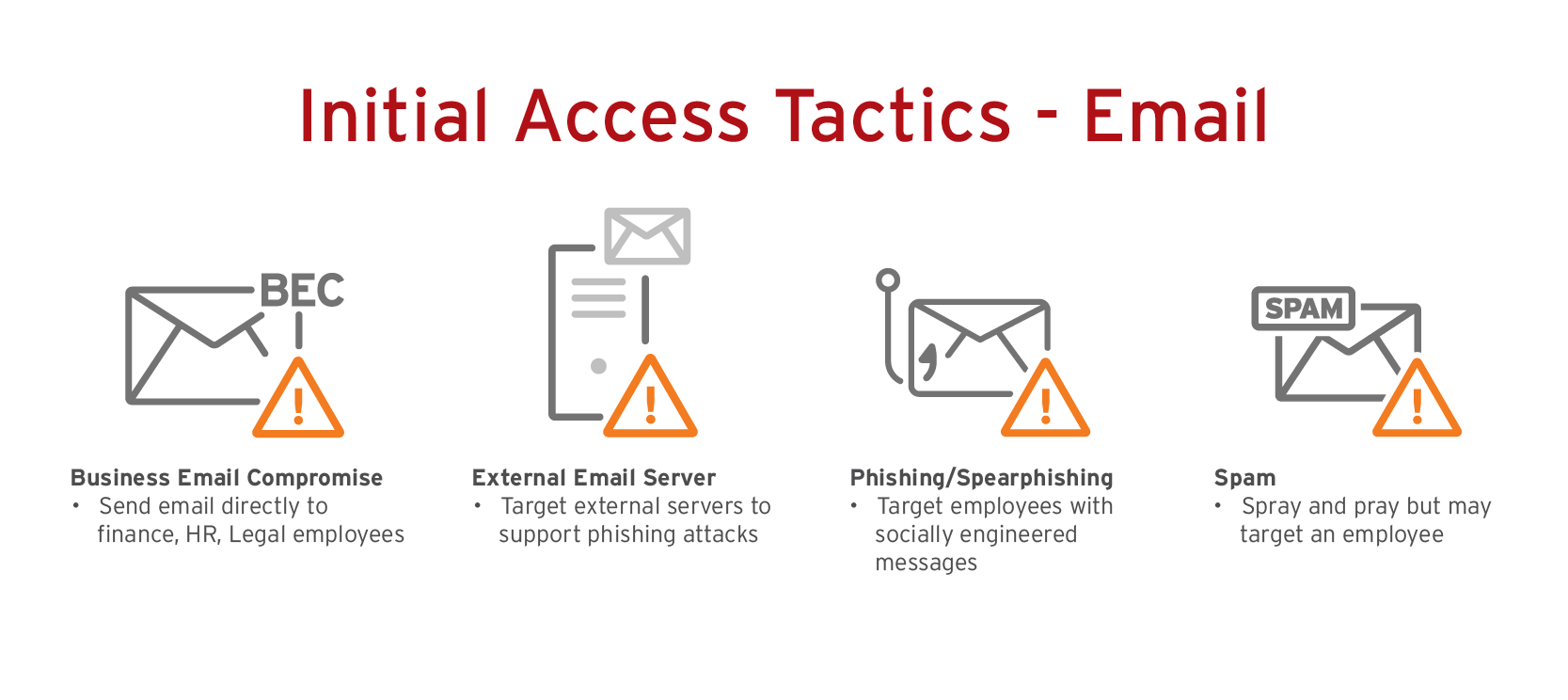
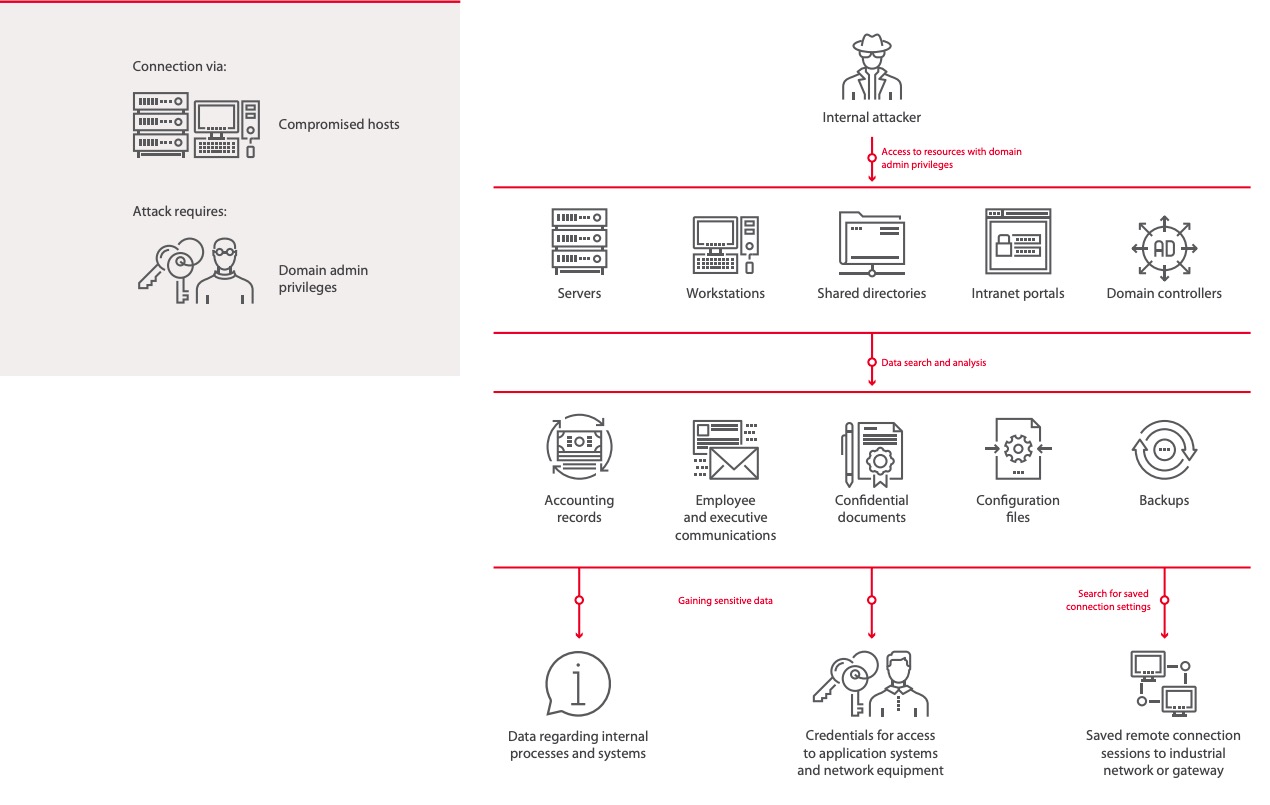
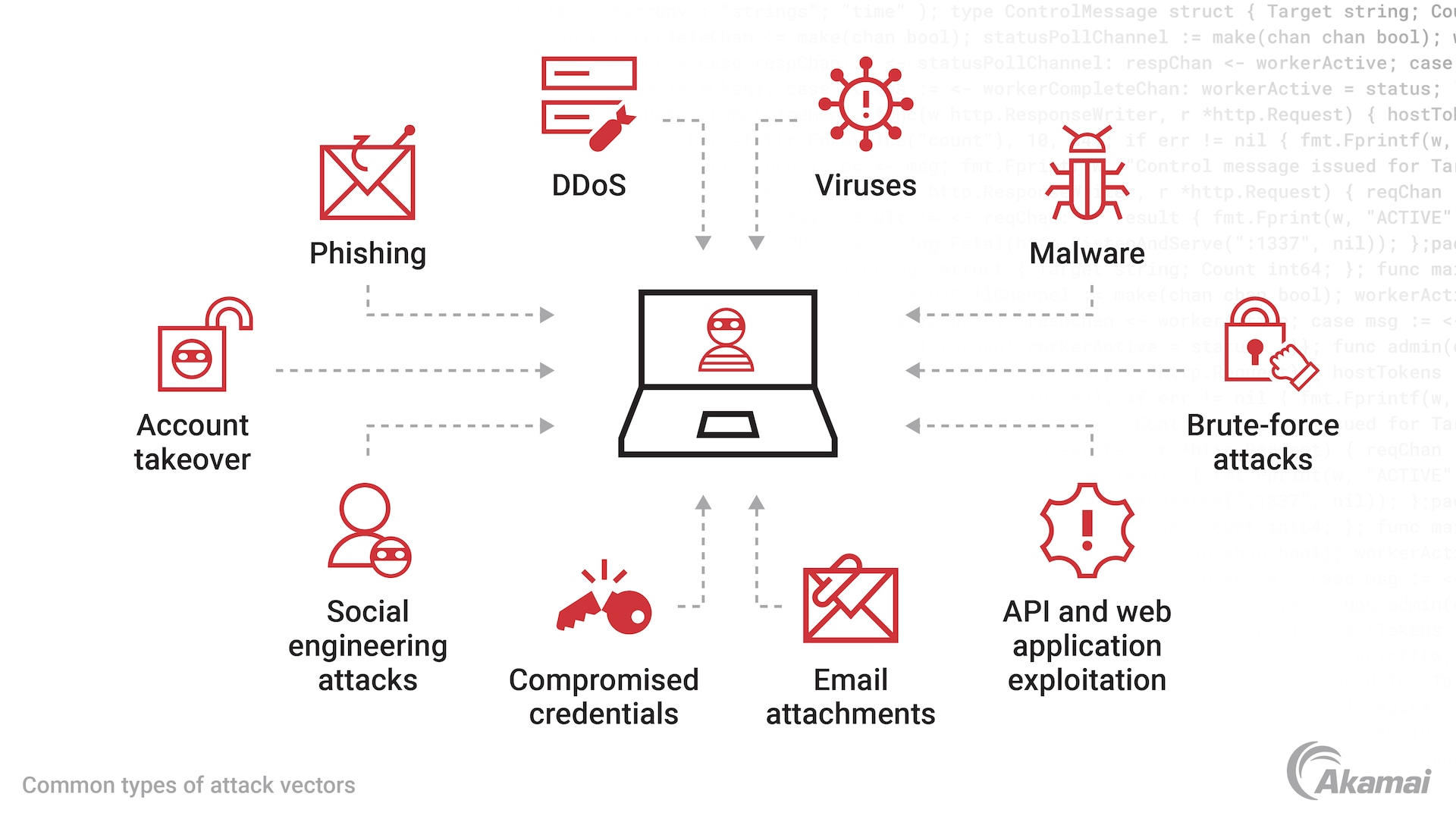
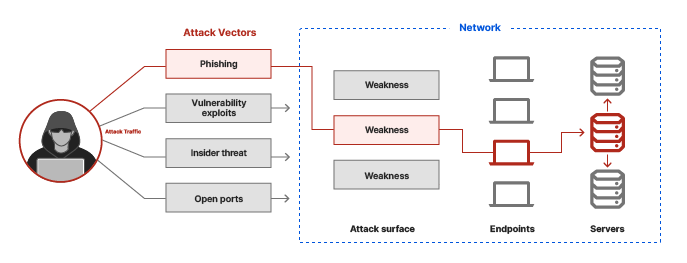
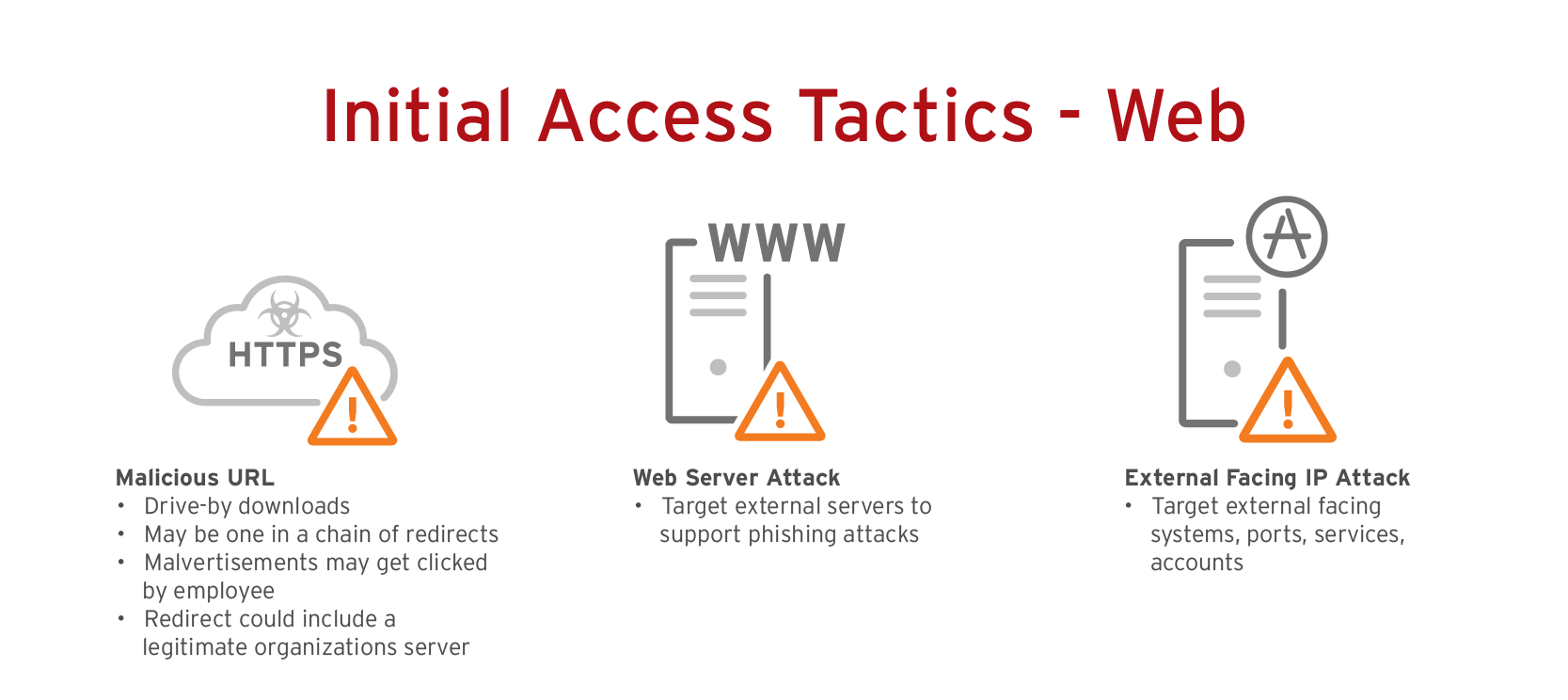
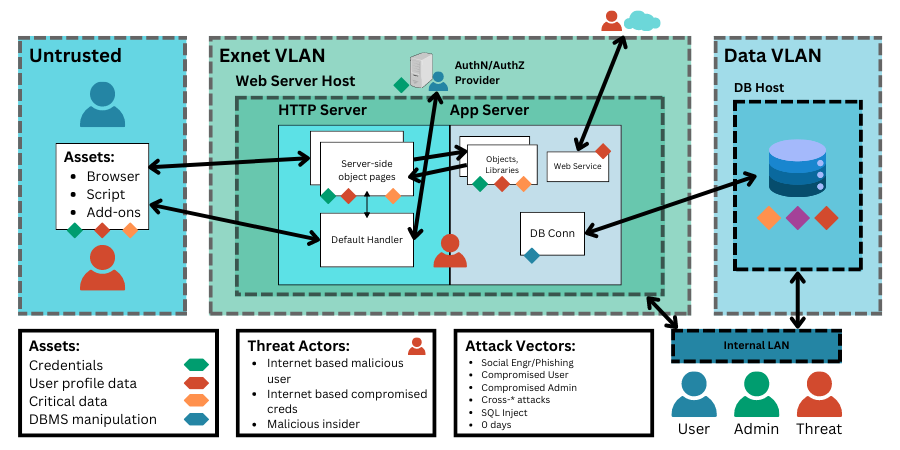
Cybersecurity Prism - What is an Attack Vector? In the context of information security, an attack vector is a specific path, method, or scenario that can be exploited by attackers to break