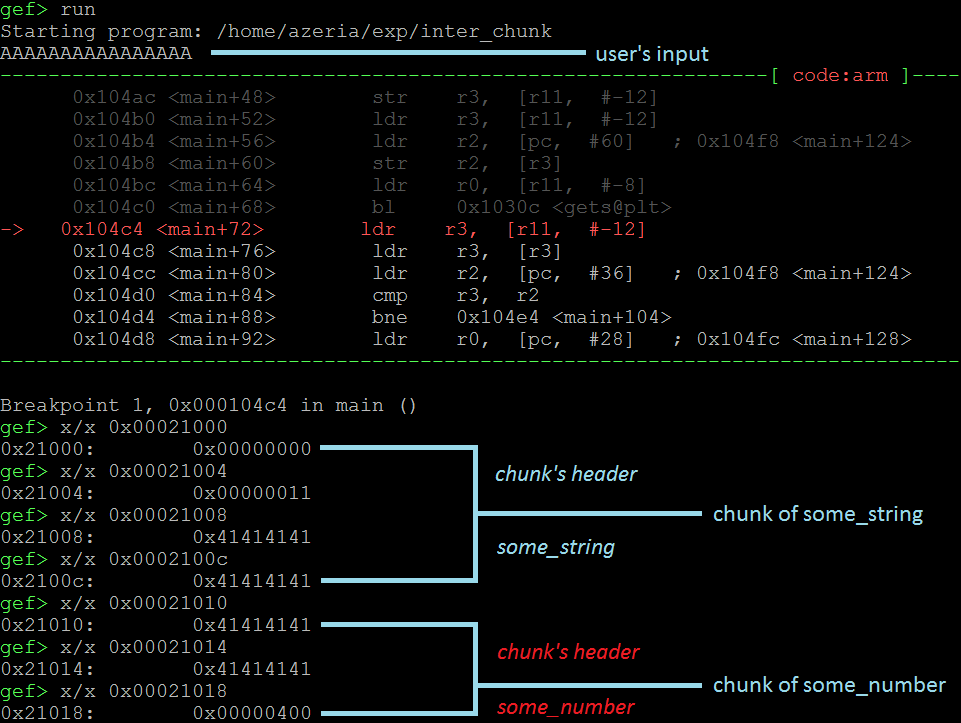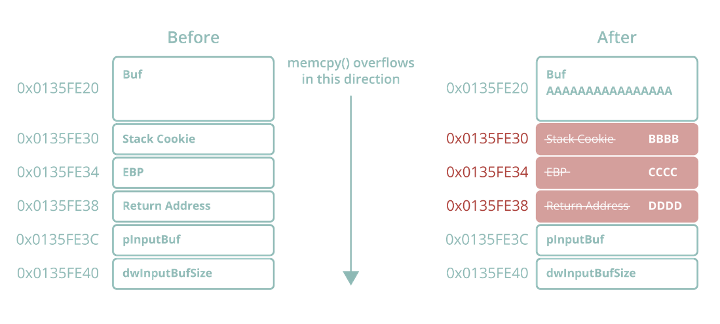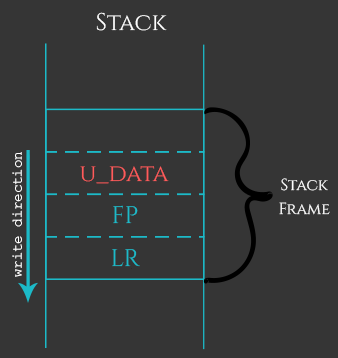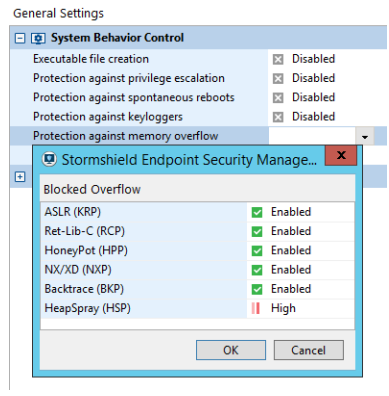
Java vs C++: Trading UB for Semantic Memory Leaks (Same Problem, Different Punishment for Failure) - IT Hare on Soft.ware
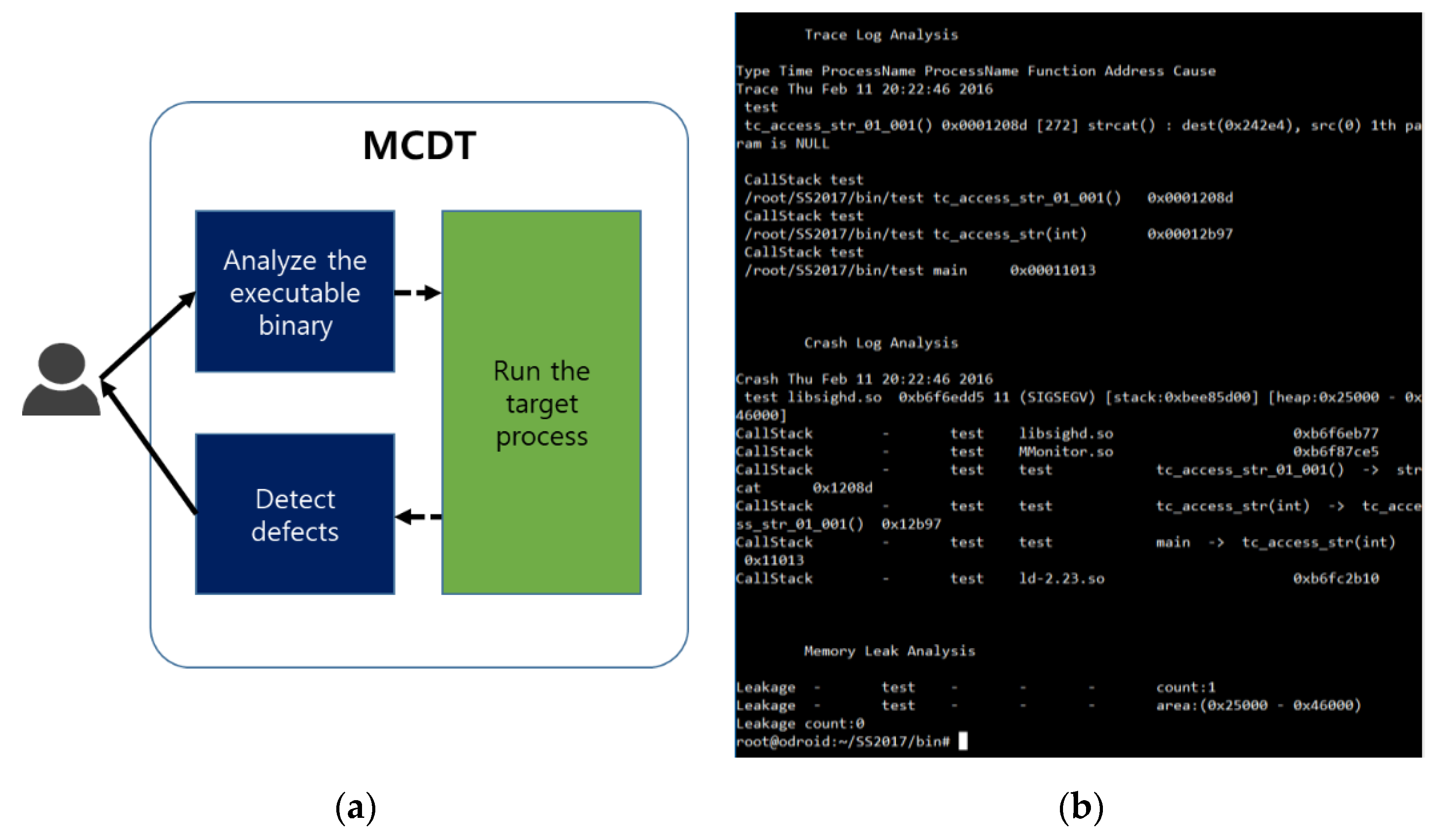
Electronics | Free Full-Text | Automated Memory Corruption Detection through Analysis of Static Variables and Dynamic Memory Usage

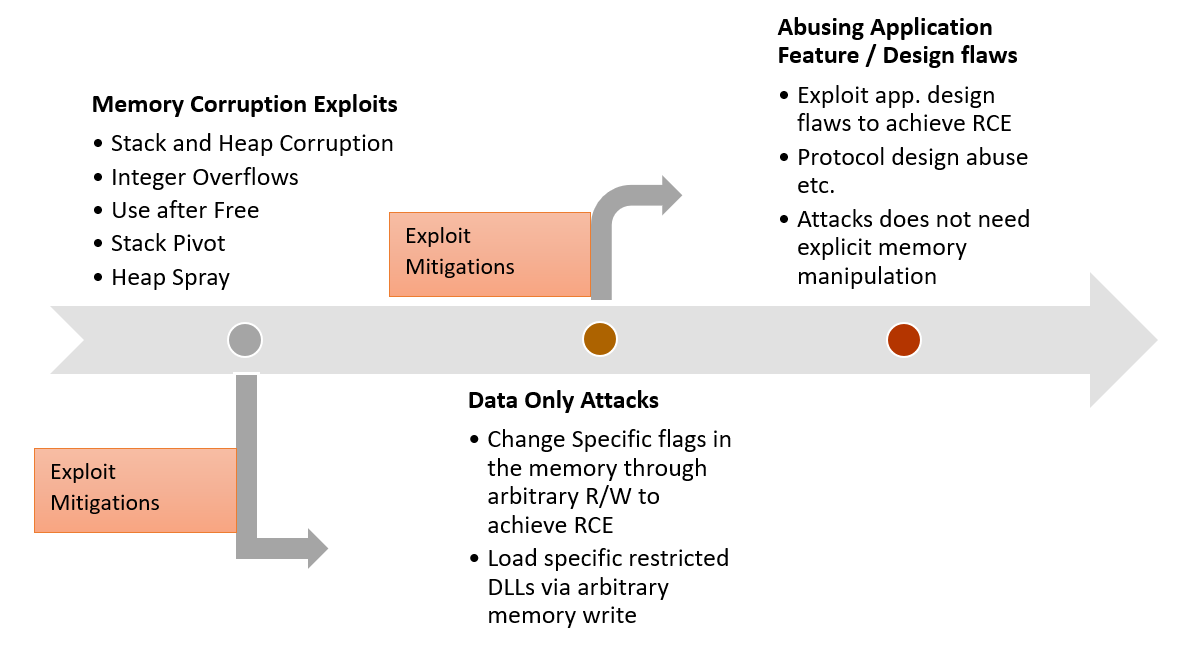
State transition of a randomized program under a memory corruption attack | Download Scientific Diagram

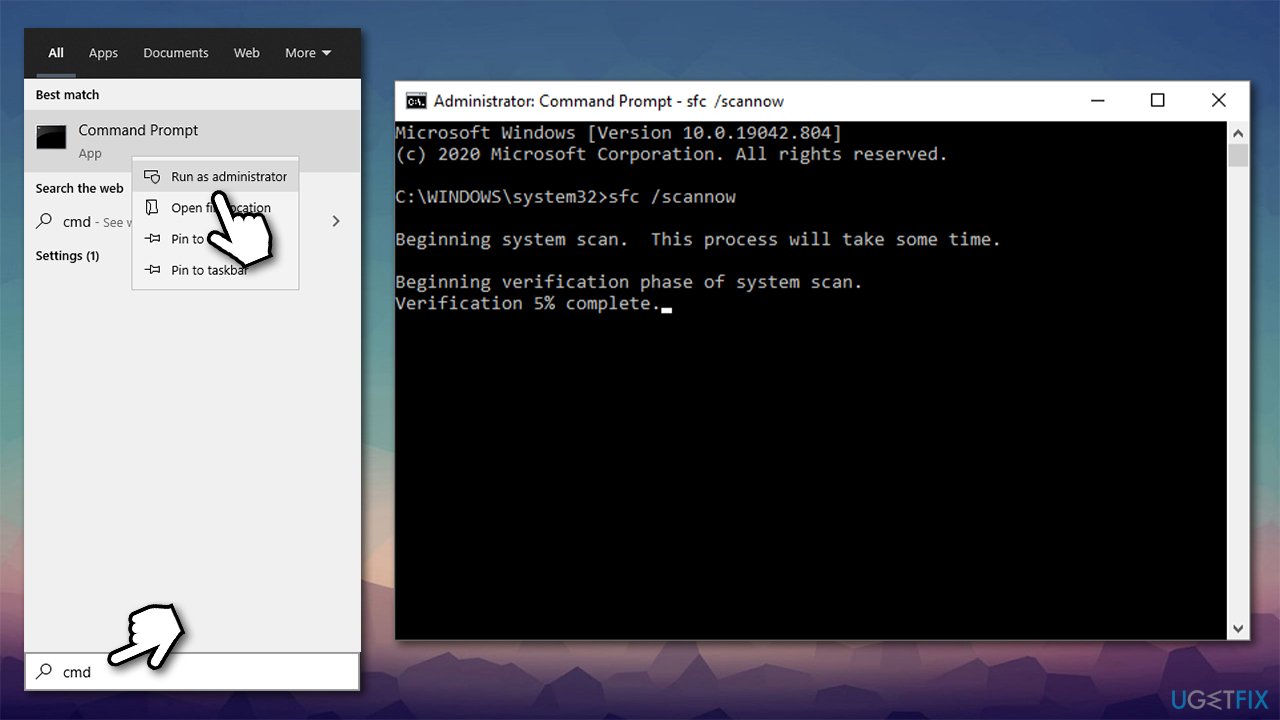
Memory Leak Tutorial | What is Memory Leak | Memory Leaks and Memory Leakage explained with Example - YouTube