
State transition of a randomized program under a memory corruption attack | Download Scientific Diagram

KMO: Kernel Memory Observer to Identify Memory Corruption by Secret Inspection Mechanism | SpringerLink
Detection of the kernel memory corruption of the LSM function pointer. | Download Scientific Diagram

Automatic Diagnosis and Response to Memory Corruption Vulnerabilities Authors: Jun Xu, Peng Ning, Chongkyung Kil, Yan Zhai, Chris Bookholt Cyber Defense. - ppt download





![PDF] Defeating memory corruption attacks via pointer taintedness detection | Semantic Scholar PDF] Defeating memory corruption attacks via pointer taintedness detection | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/4a4d61347bb00e73a6a80cdcf18b49da1dba5adb/3-Figure2-1.png)






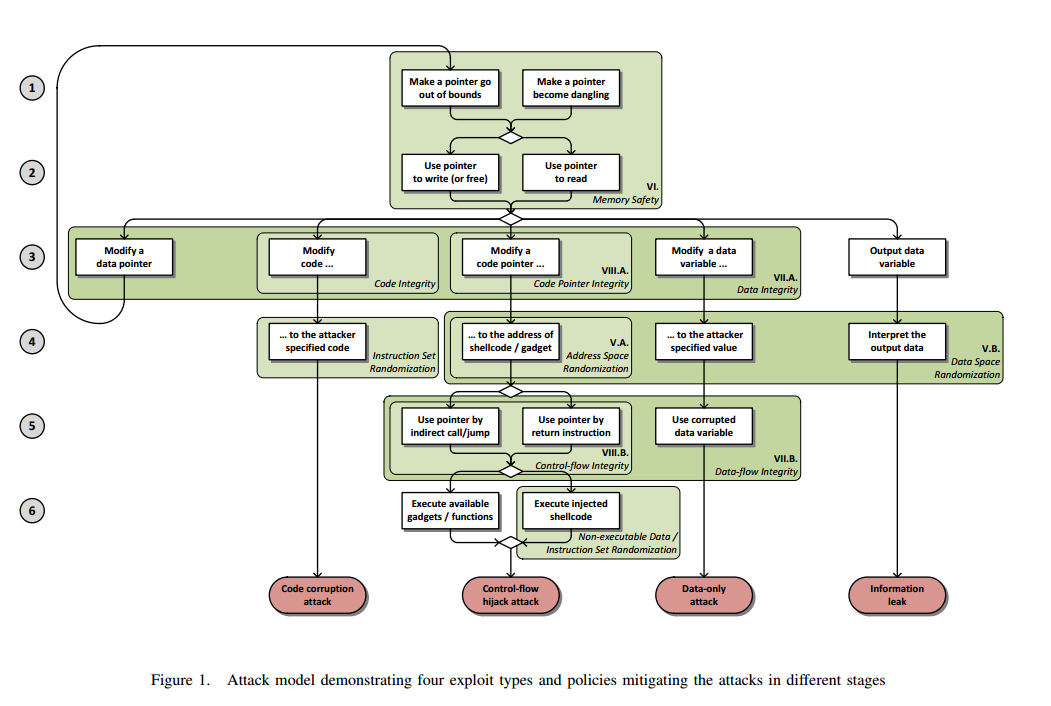
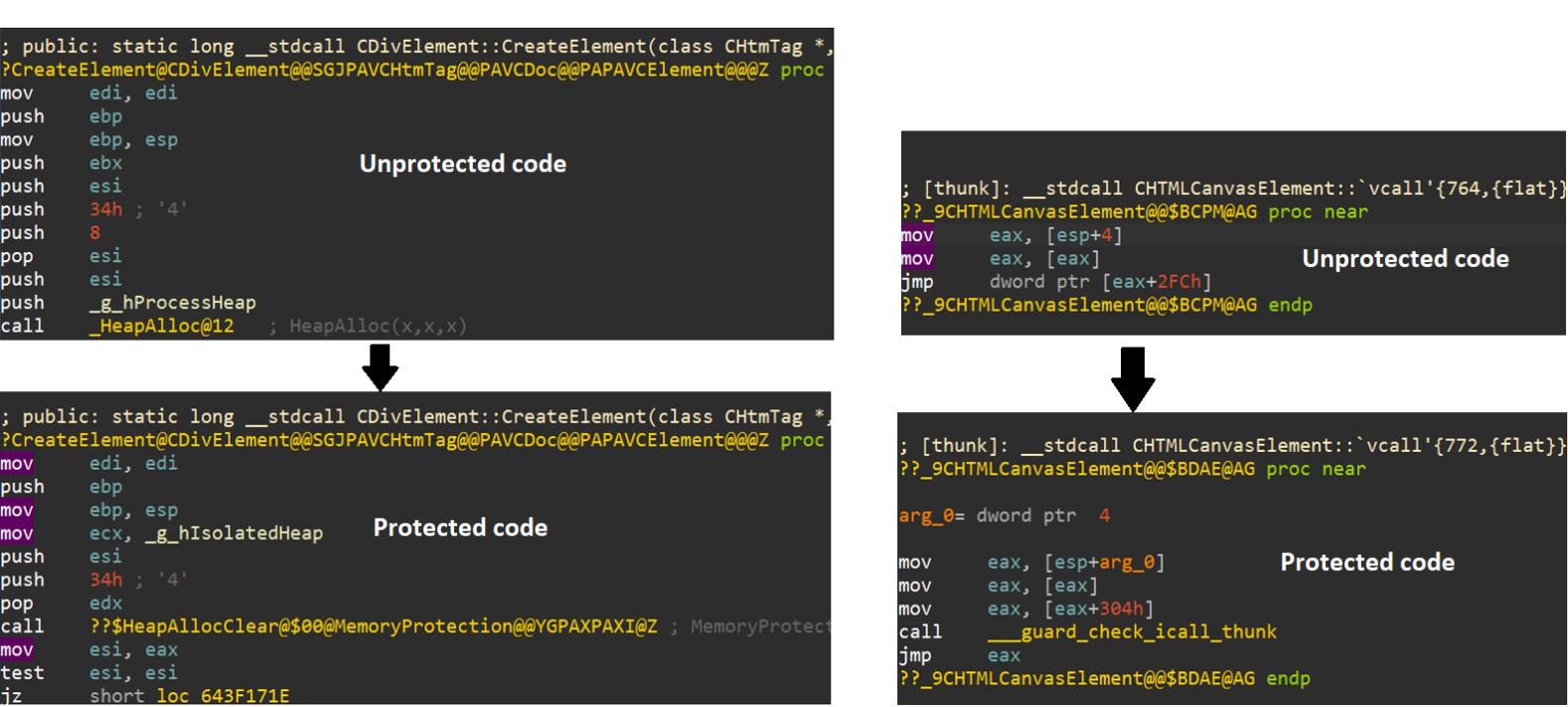
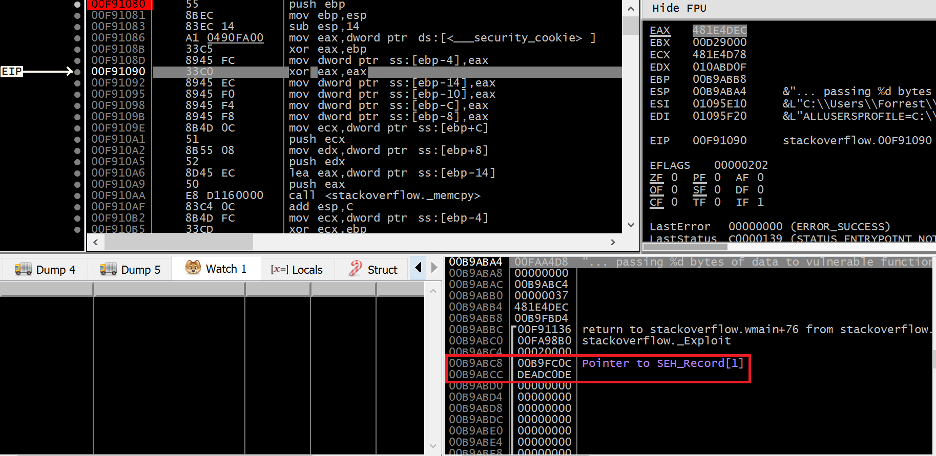
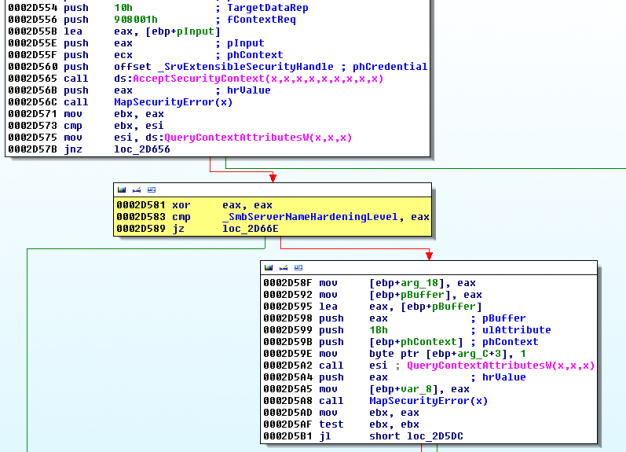
![Memory corruption vulnerabilities - Advanced Infrastructure Penetration Testing [Book] Memory corruption vulnerabilities - Advanced Infrastructure Penetration Testing [Book]](https://www.oreilly.com/api/v2/epubs/9781788624480/files/assets/dd59478e-ba14-48db-ba7e-cfe33bfed00b.png)