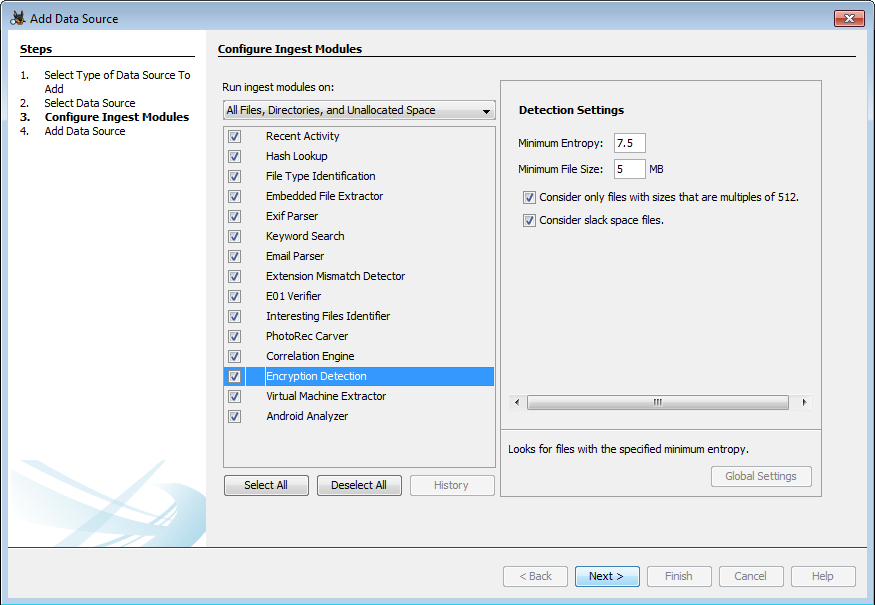
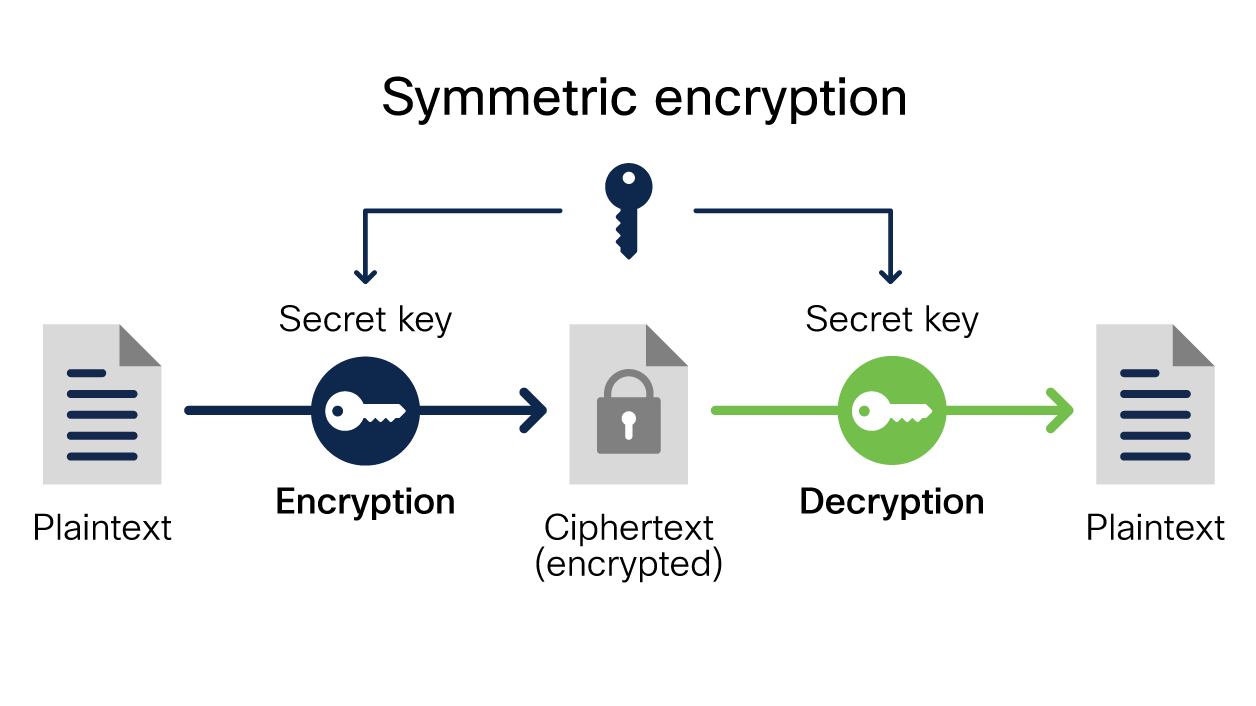
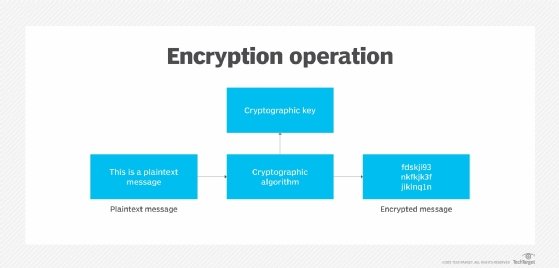
An efficient chaos-based image encryption algorithm using real-time object detection for smart city applications - ScienceDirect
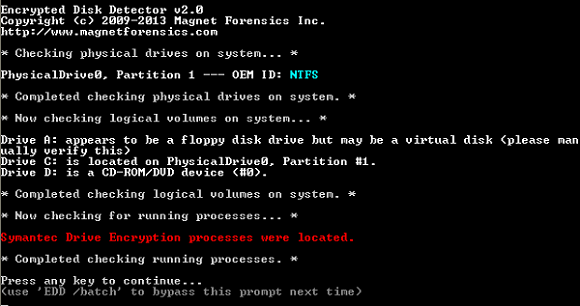
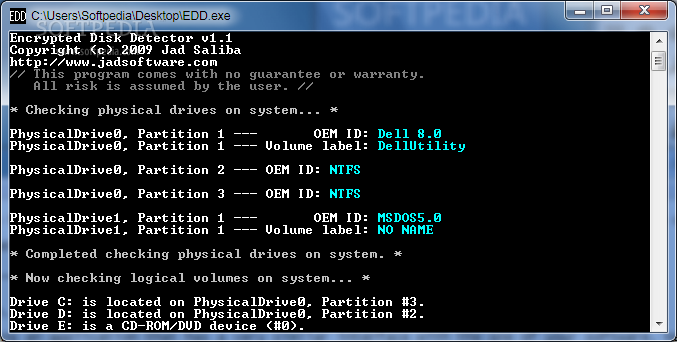
SANS Digital Forensics and Incident Response Blog | Encrypted Disk Detector Version 2 | SANS Institute

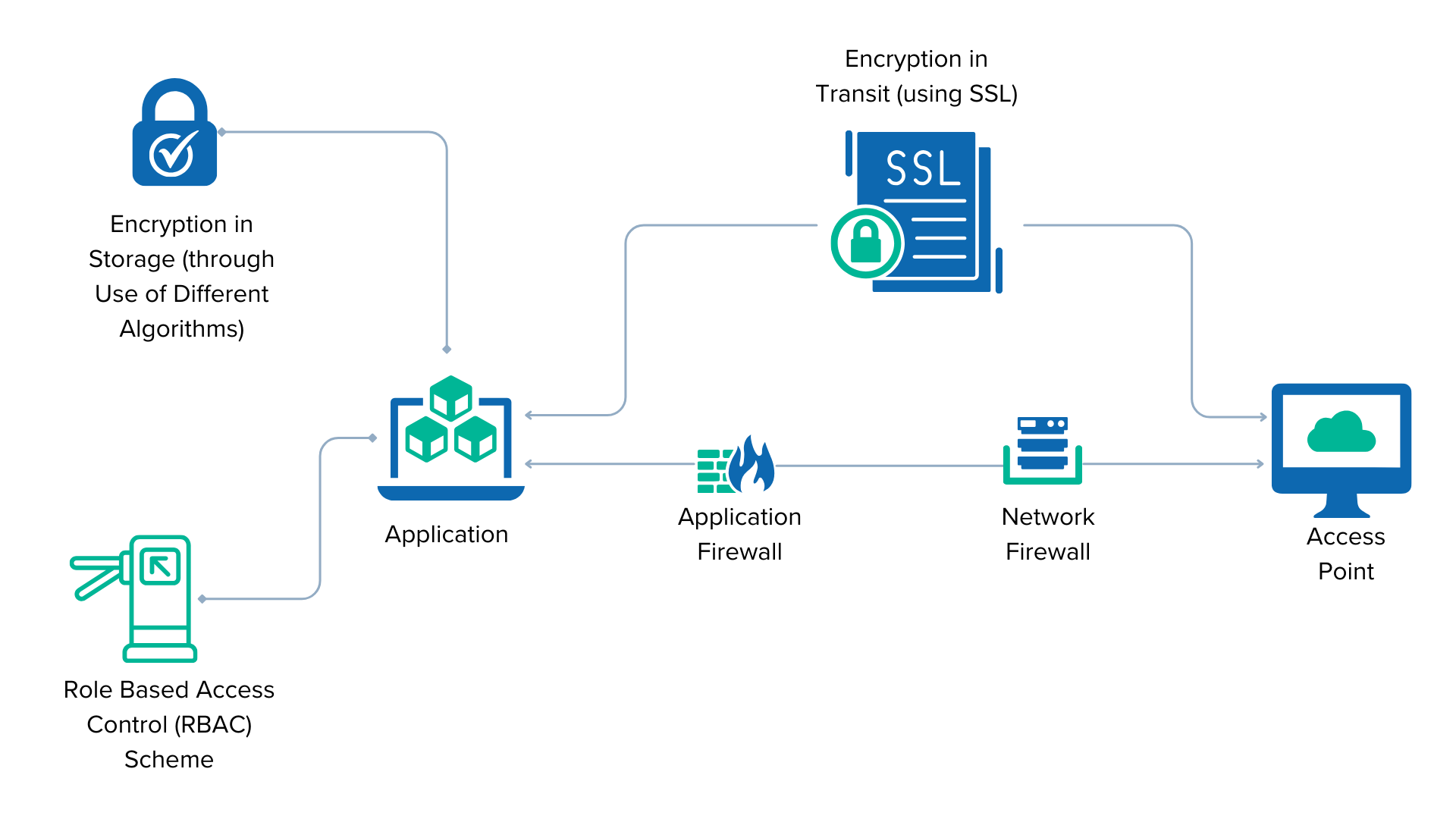
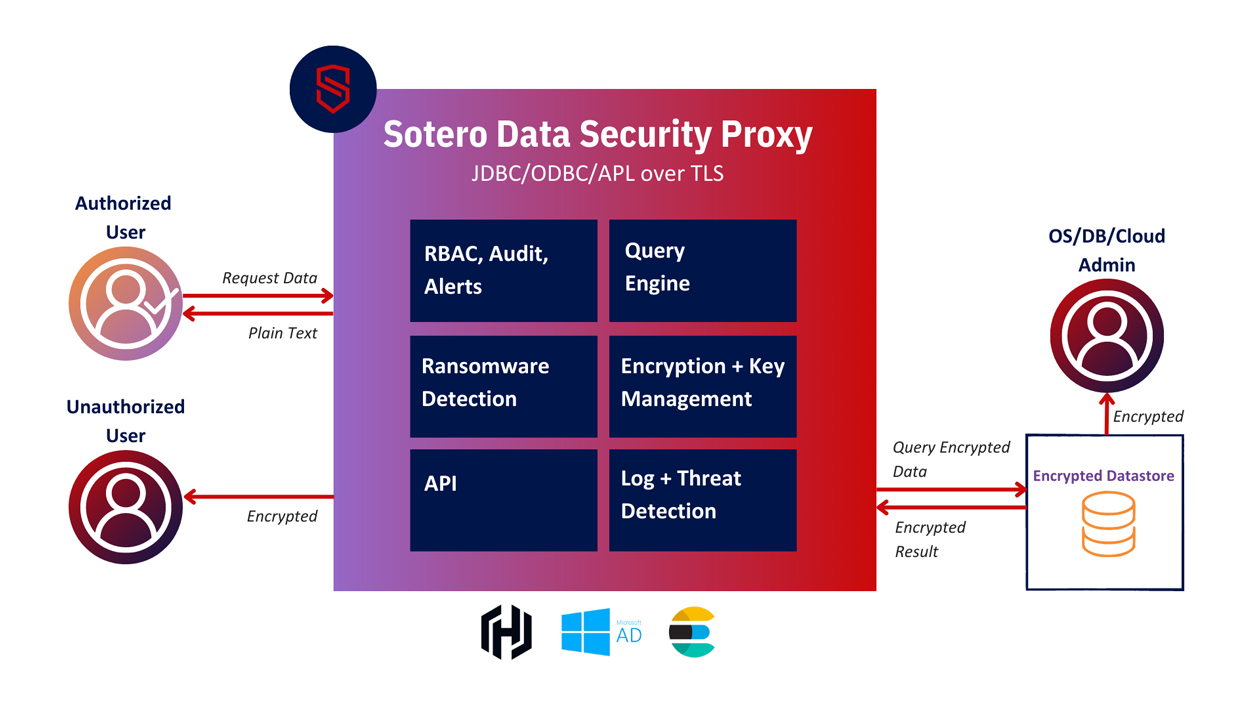
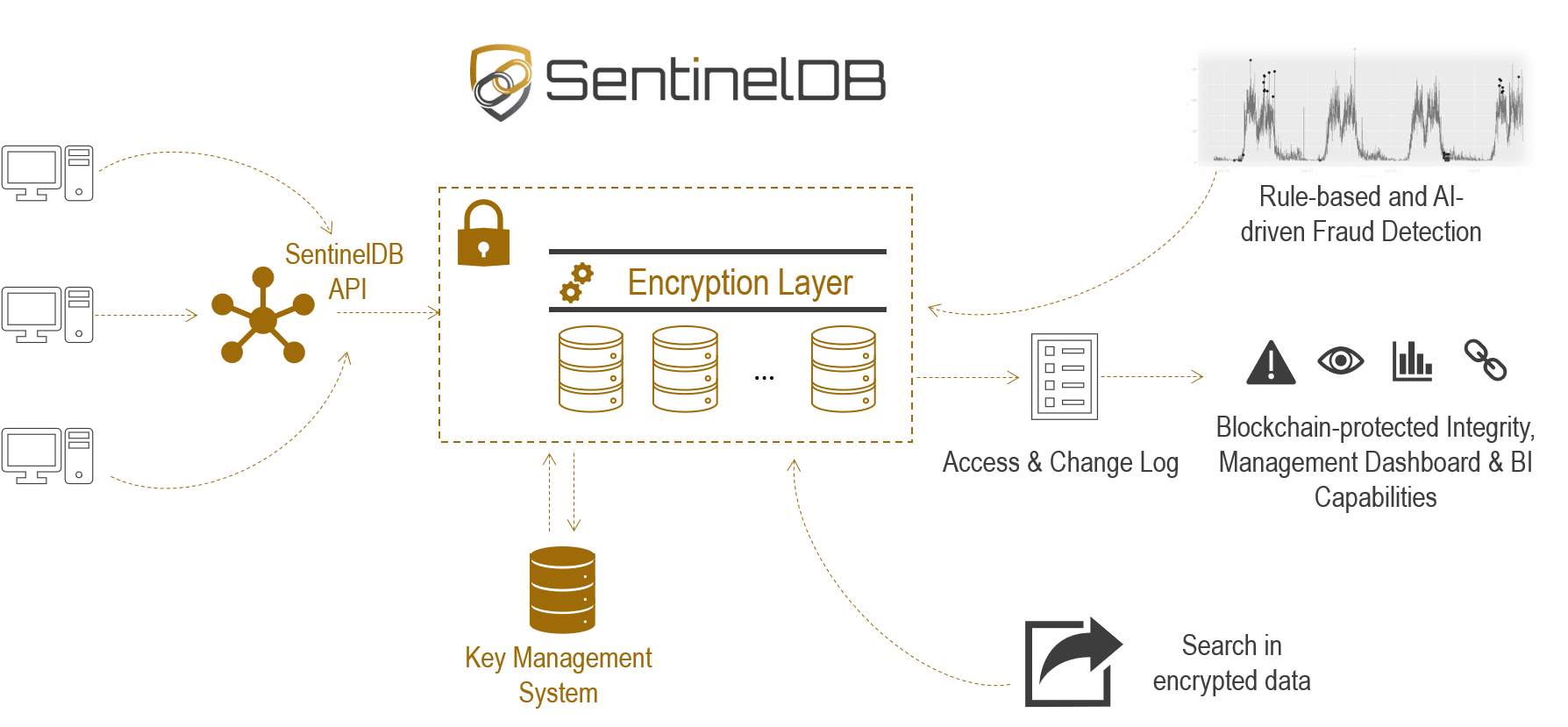
GitHub - cossacklabs/acra: Database security suite. Database proxy with field-level encryption, search through encrypted data, SQL injections prevention, intrusion detection, honeypots. Supports client-side and proxy-side ("transparent") encryption ...

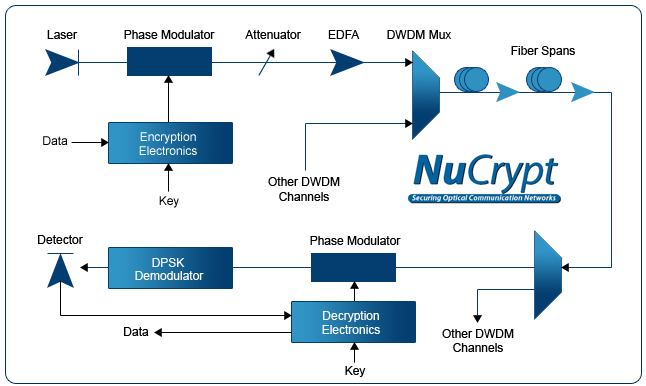
Drones | Free Full-Text | A New Image Encryption Algorithm Based on DNA State Machine for UAV Data Encryption
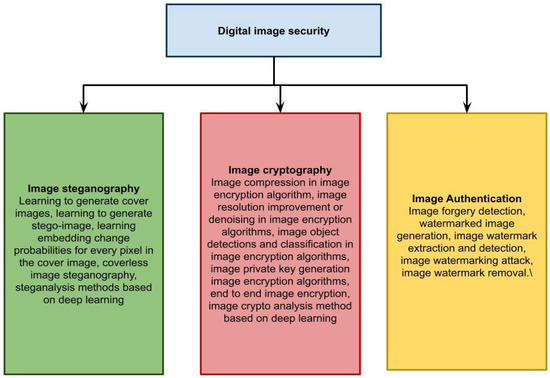
Sensors | Free Full-Text | Face Image Encryption Based on Feature with Optimization Using Secure Crypto General Adversarial Neural Network and Optical Chaotic Map
Machine learning over encrypted data for fault detection applications. | Download Scientific Diagram