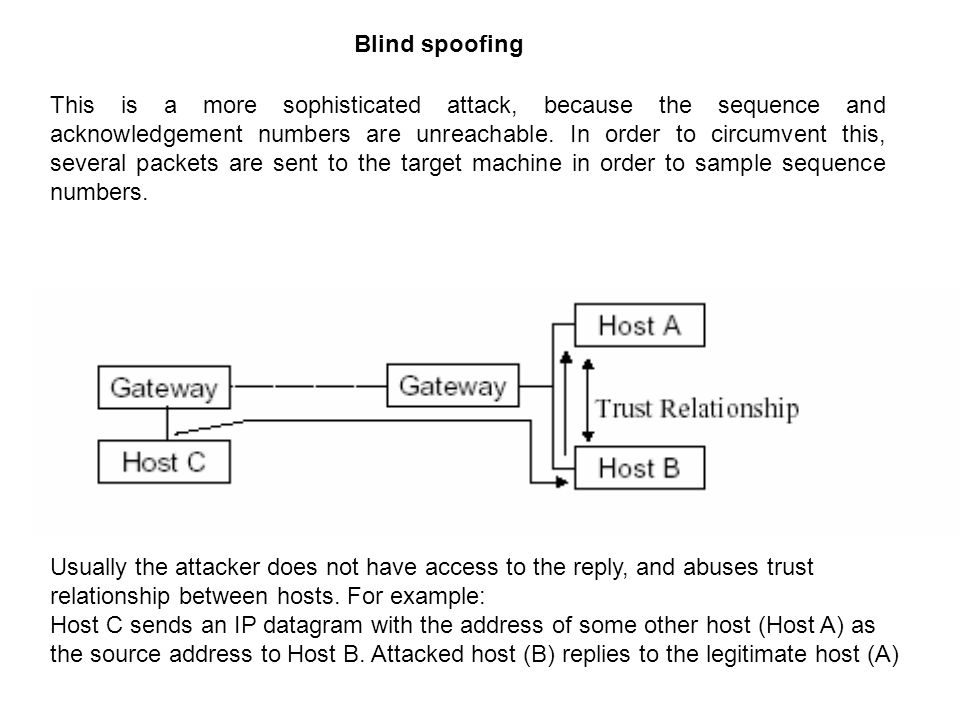
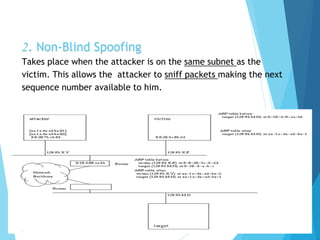
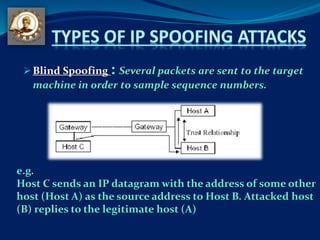
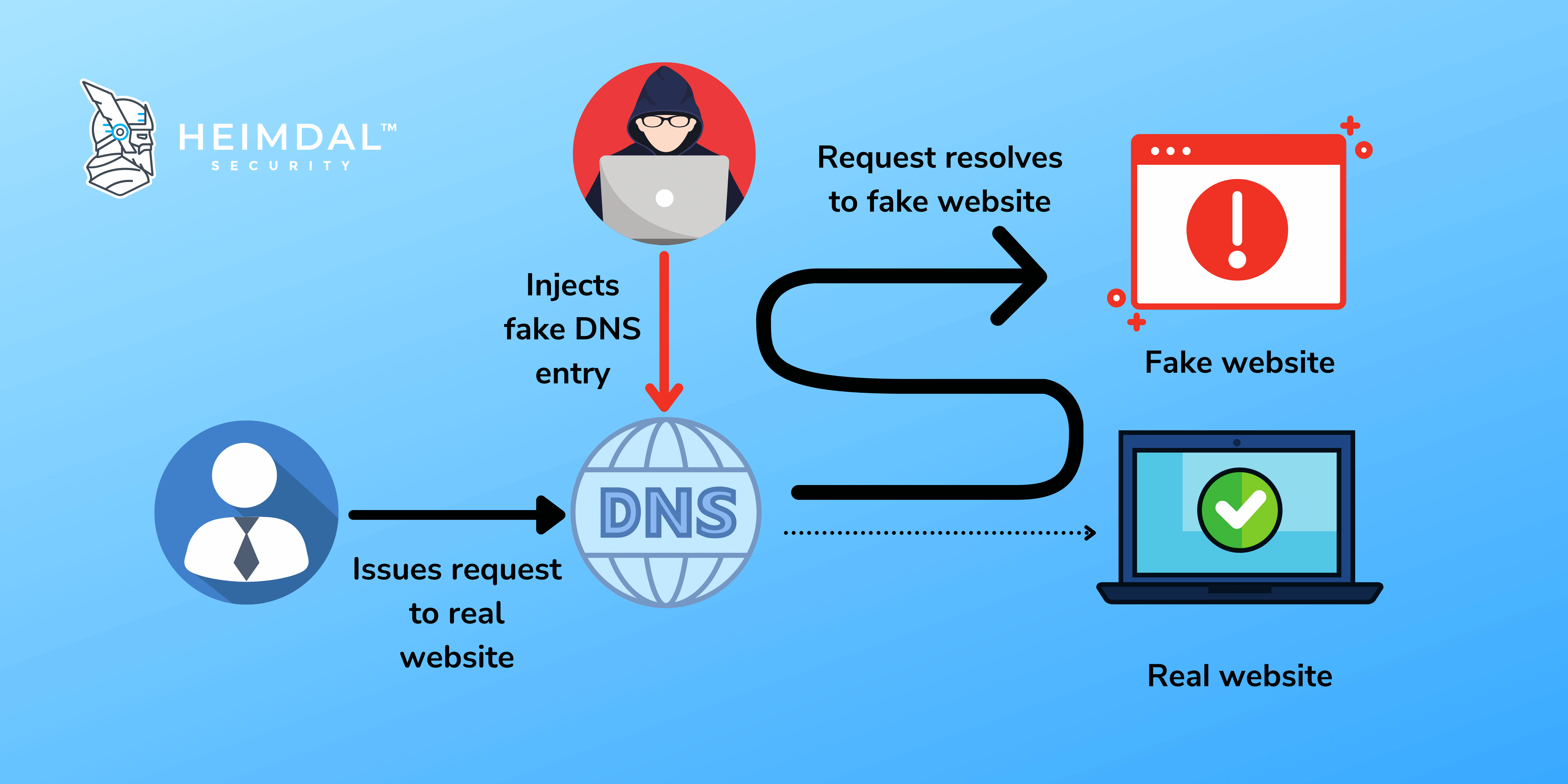
Discuss with examples the following: i) ARP spoofing iii) TCP syn flood attack ii) Port scanning iv) IP spoofing
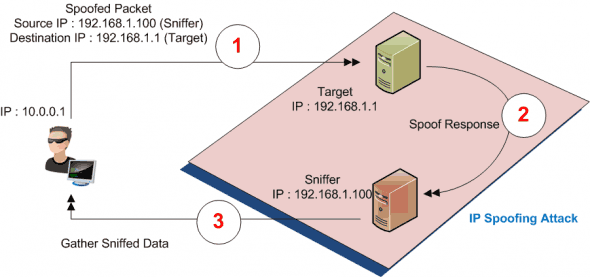
Packet Sniffing Protection Security Services | Pune Mumbai Hyderabad Delhi Bangalore India | Valency Networks
PPT - Suneeta Chawla Web Security Presentation Topic : IP Spoofing Date : 03/24/04 PowerPoint Presentation - ID:903222
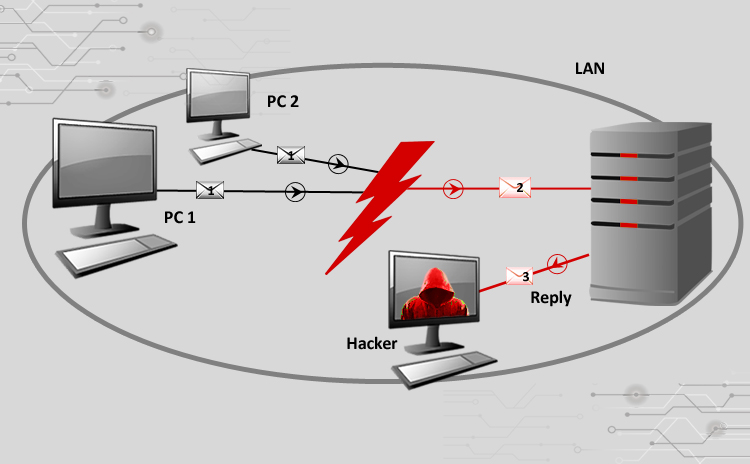
Cyber Attacks Explained - Packet Spoofing - Cyber Security Blogs - Valency Networks - Best VAPT Penetration Testing Cyber Security Company - Pune Mumbai Hyderabad Delhi Bangalore Ahmedabad Kolkata India Dubai Bahrain

Hacking Tricks - <3 IP spoofing <3 IP spoofing, also known as IP address forgery or a host file hijack, is a hijacking technique in which a cracker masquerades as a trusted
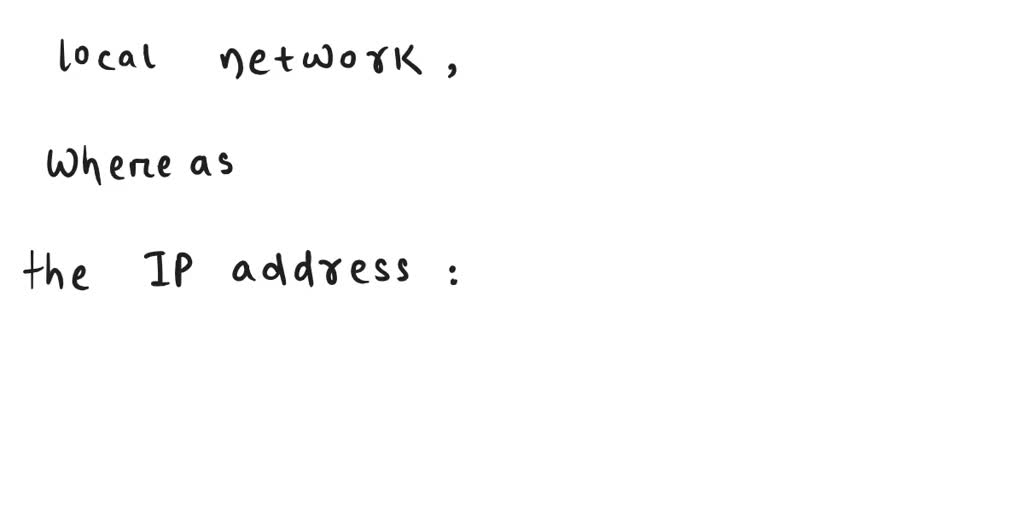
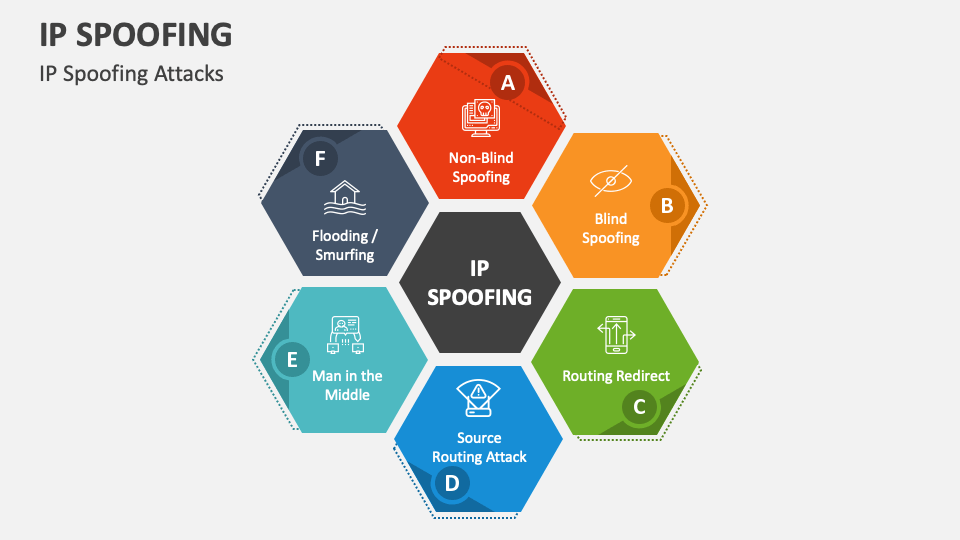
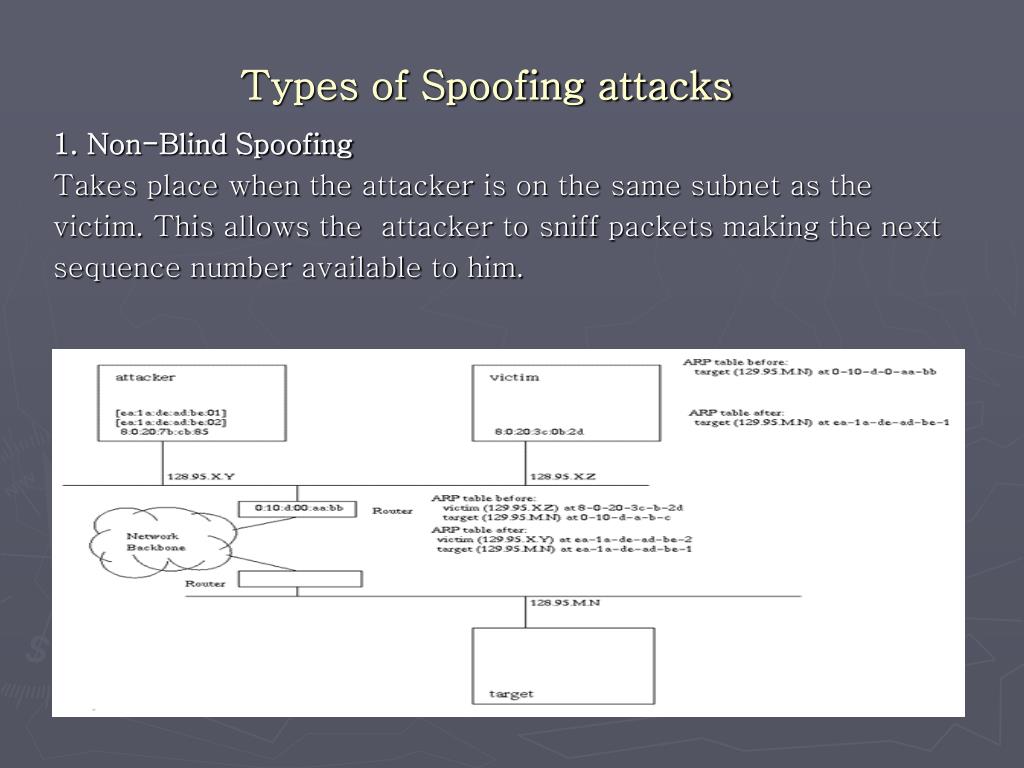
VIDEO solution: Explain why give more explain to teach me EIE3120 Network Technologies and Security. There are four kinds of IP spoofing attacks: blind spoofing, non-blind spoofing, denial-of-service attack, and man-in-the-middle attack.